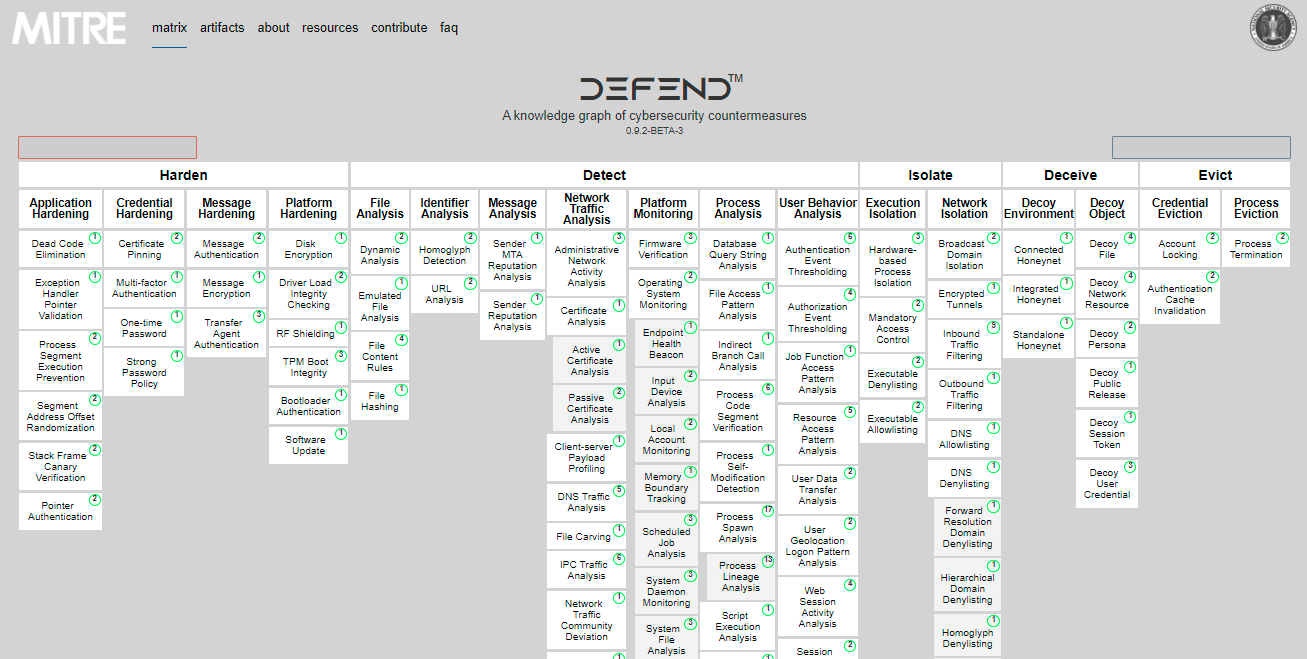
Recently a Framework was Released by NSA named D3FEND which is based on and Complementary to MITRE ATT&CK Framework. It gave a Technical Knowledge base to create Defensive Countermeasure against Common Offensive techniques. D3FEND, a framework for cybersecurity professionals to tailor defenses against specific cyber threats is now available through MITRE. NSA funded MITRE’s research… Continue reading NSA Released D3FEND a framework for cybersecurity professionals to tailor defenses
Month: July 2021
MITRE ATT&CK® Released Updates in April 2021 With Additional Techniques and Structuring
MITRE ATT&CK® is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. With the creation of ATT&CK, MITRE… Continue reading MITRE ATT&CK® Released Updates in April 2021 With Additional Techniques and Structuring
Bharat Ranked in Tier 3 of IISS Cyber Capabilities and National Power: A Net Assessment
As a result of a Study conducted by IISS Researchers in the last two years, Bharat was ranked in Tier 3, it is to be noted that the US is the only nation in Tier one. Instead of Going the traditional way of indexing Nations on basis of only cybersecurity capability, they have gone qualitatively… Continue reading Bharat Ranked in Tier 3 of IISS Cyber Capabilities and National Power: A Net Assessment
Penetration testing Attack Infrastructure
Attack Infra Penetration testing Planning Fill the planning gap Attack Infrastructure/C2 Recon Social Engineering Weaponization Initial Access/foothold Network Propagation Action on Objectives Mitre Attack Framework Pre attack framework is to be followed. The MITRE ATT&CK™ framework is a comprehensive matrix of tactics and techniques used by threat hunters, red teamers, and defenders to better classify attacks and assess an organization’s risk… Continue reading Penetration testing Attack Infrastructure