Google has just patched a critical zero-day vulnerability in its Chrome web browser—CVE-2025-10585—which has been actively exploited in the wild. This flaw,
Vulnerability
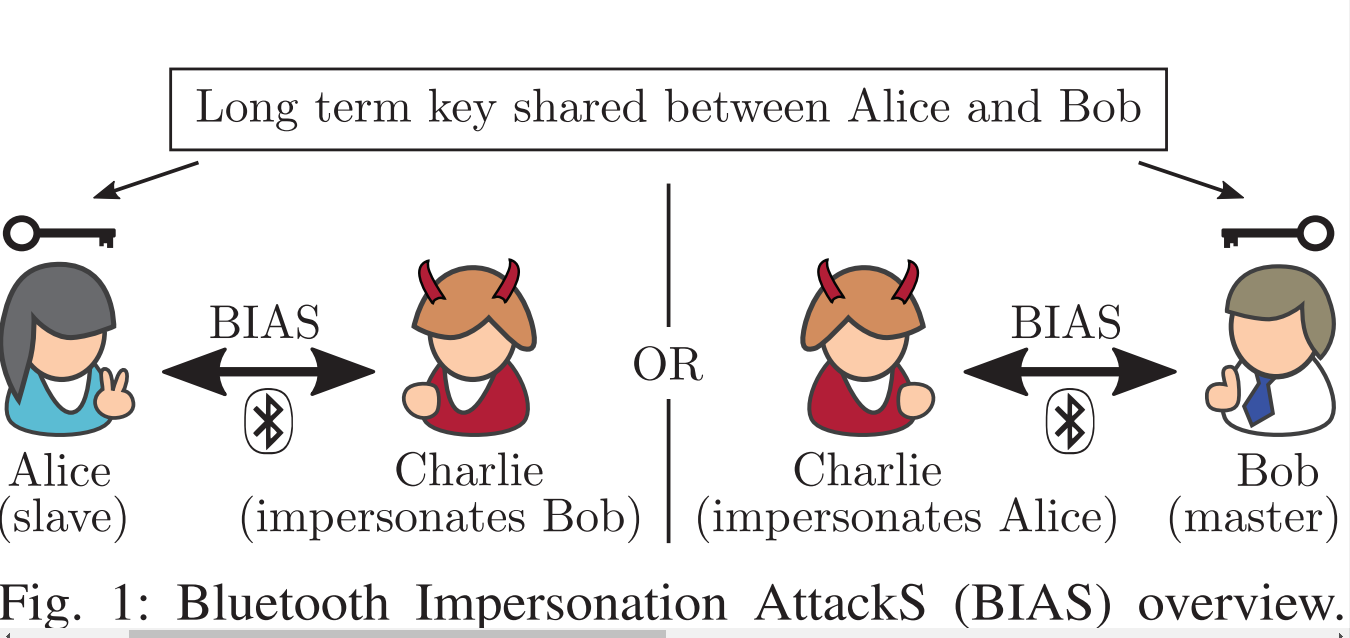
BIAS: Bluetooth Impersonation AttackS
Daniele Antonioli (Postdoc at the EPFL Cyber-Physical Systems Security, Network Security, Wireless Security, Embedded Systems Security, Applied Cryptography, SoCurity) ,
Cyber Espionage

Portuguese NATO documents discovered for sale online
The National Security Office is still determining the extent of the damage, but EMGFA, secret military, and MDN computers are
Geopolitics

Pakistan-Linked APT36 Exploits “Pahalgam Terror Attack” Theme in Multi-Pronged Cyber Espionage Campaign Against India
In a recent and concerning development in the ongoing cyber conflict landscape, the Pakistan-linked Advanced Persistent Threat (APT) group known
Latest Posts
Malware Analysis Report on a malicious listener deployed on Ivanti Endpoint Manager Mobile (EPMM) systems
U.S. Cybersecurity and Infrastructure Security Agency’s new Malware Analysis Report on a malicious listener deployed on Ivanti Endpoint Manager Mobile
Critical Google Chrome Zero-Day CVE-2025-10585: What You Need to Know
Google has just patched a critical zero-day vulnerability in its Chrome web browser—CVE-2025-10585—which has been actively exploited in the wild. This flaw,
CISA Issues Nine Urgent Advisories on Industrial Control Systems Vulnerabilities
In a critical bulletin released on September 18, 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) published nine new

MSSP Alert Top 250 for 2024: A Deep Dive into the State of Cybersecurity
Discover the key findings from the 2024 MSSP Alert Top 250 report. Explore trends in MSSP growth, profitability, in-house SOCs, and the critical services defining modern cyber defense.