MITRE ATT&CK® Released Updates in Apr 2022 With Additional Techniques and Structuring
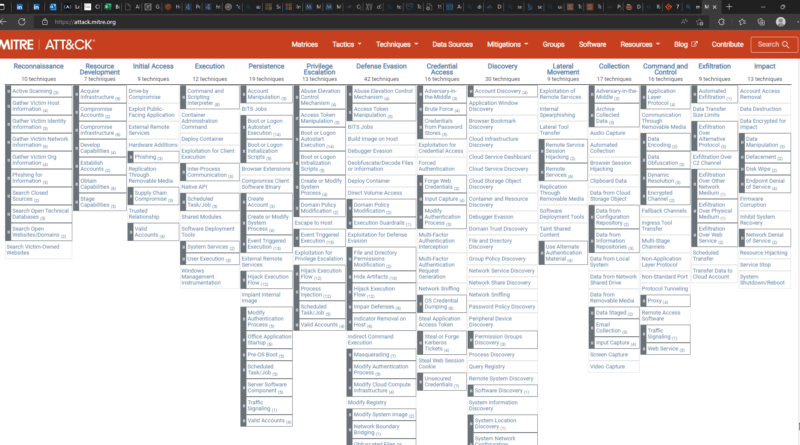
The Techniques, Groups, and Software for Enterprise, Mobile, and ICS are updated in the April 2022 (v11) ATT&CK release. The most significant modifications are the reorganisation of Detections, which are now connected to Data Source and Data Component objects in Enterprise ATT&CK, the beta release of ATT&CK for Mobile using sub-techniques, and the addition of ATT&CK for ICS to attack.mitre.org. These adjustments as well as enhancements across ATT&CK’s various domains and platforms are detailed in an accompanying blog post.
A beta version of ATT&CK for Mobile is included in this release and is displayed using sub-techniques. You can still access the most recent stable version of ATT&CK for Mobile at https://attack.mitre.org/versions/v10/matrices/mobile/. An accompanying blog post provides instructions on how to upgrade to this new version of ATT&CK for Mobile. Our GitHub repository contains a rendering of this beta content done in STIX.
In order to better reflect adversary behaviour, we have changed the Enterprise Sub-Techniques Boot or Logon Autostart Execution: Plist Modification (T1547.011) and Scheduled Task/Job: At (Linux)(T1053.001) into Plist File Modification (T1647) and Scheduled Task/Job: At (T1053.002), respectively.

14 Tactics, 191 Techniques, 386 Sub-techniques, 134 Groups, and 680 Pieces of Software make up this version of ATT&CK for Enterprise.
Techniques
Enterprise
New Techniques
- Account Manipulation: Device Registration
- Active Scanning: Wordlist Scanning
- Adversary-in-the-Middle: DHCP Spoofing
- Debugger Evasion
- Hide Artifacts: Process Argument Spoofing
- Hijack Execution Flow: KernelCallbackTable
- Inter-Process Communication: XPC Services
- Modify Authentication Process: Reversible Encryption
- Multi-Factor Authentication Request Generation
- Plist File Modification
- Process Injection: ListPlanting
- Server Software Component: Terminal Services DLL
Technique changes
- Abuse Elevation Control Mechanism: Setuid and Setgid
- Account Access Removal
- Account Manipulation
- Additional Cloud Credentials
- Additional Cloud Roles
- Additional Email Delegate Permissions
- SSH Authorized Keys
- Adversary-in-the-Middle
- Application Window Discovery
- Archive Collected Data: Archive via Utility
- Automated Collection
- Boot or Logon Autostart Execution: Kernel Modules and Extensions
- Boot or Logon Autostart Execution: Port Monitors
- Boot or Logon Autostart Execution: Re-opened Applications
- Boot or Logon Initialization Scripts: Login Hook
- Brute Force
- Password Cracking
- Password Guessing
- Build Image on Host
- Cloud Infrastructure Discovery
- Command and Scripting Interpreter
- PowerShell
- Visual Basic
- Compromise Infrastructure
- DNS Server
- Domains
- Container Administration Command
- Create Account: Cloud Account
- Create or Modify System Process
- Launch Agent
- Windows Service
- Credentials from Password Stores: Keychain
- Credentials from Password Stores: Securityd Memory
- Data Encrypted for Impact
- Data Manipulation
- Runtime Data Manipulation
- Stored Data Manipulation
- Transmitted Data Manipulation
- Data Staged
- Local Data Staging
- Data from Local System
- Defacement
- External Defacement
- Internal Defacement
- Deploy Container
- Drive-by Compromise
- Endpoint Denial of Service: Application Exhaustion Flood
- Endpoint Denial of Service: Application or System Exploitation
- Endpoint Denial of Service: OS Exhaustion Flood
- Endpoint Denial of Service: Service Exhaustion Flood
- Escape to Host
- Event Triggered Execution: PowerShell Profile
- Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol
- Exfiltration Over Other Network Medium: Exfiltration Over Bluetooth
- Exploitation for Client Execution
- File and Directory Discovery
- Firmware Corruption
- Gather Victim Identity Information
- Email Addresses
- Hardware Additions
- Hide Artifacts: Email Hiding Rules
- Hide Artifacts: Hidden Users
- Hide Artifacts: Hidden Window
- Hijack Execution Flow
- Impair Defenses: Disable Cloud Logs
- Impair Defenses: Downgrade Attack
- Impair Defenses: Impair Command History Logging
- Implant Internal Image
- Indicator Removal on Host
- Clear Command History
- Clear Windows Event Logs
- File Deletion
- Ingress Tool Transfer
- Inhibit System Recovery
- Input Capture: GUI Input Capture
- Inter-Process Communication
- Dynamic Data Exchange
- Internal Spearphishing
- Lateral Tool Transfer
- Modify Authentication Process
- Multi-Factor Authentication Interception
- Network Boundary Bridging
- Network Denial of Service: Direct Network Flood
- Network Denial of Service: Reflection Amplification
- Network Service Discovery
- Network Sniffing
- OS Credential Dumping: NTDS
- Obfuscated Files or Information: Software Packing
- Password Policy Discovery
- Peripheral Device Discovery
- Phishing: Spearphishing Link
- Phishing for Information: Spearphishing Link
- Pre-OS Boot: Component Firmware
- Process Injection: Process Hollowing
- Remote Access Software
- Remote Services: Remote Desktop Protocol
- Remote System Discovery
- Resource Hijacking
- Rogue Domain Controller
- Scheduled Task/Job
- At
- Container Orchestration Job
- Scheduled Task
- Server Software Component
- Software Discovery: Security Software Discovery
- Stage Capabilities: Drive-by Target
- Steal Application Access Token
- Steal or Forge Kerberos Tickets
- Kerberoasting
- Subvert Trust Controls: Mark-of-the-Web Bypass
- Supply Chain Compromise
- System Binary Proxy Execution
- CMSTP
- Compiled HTML File
- Control Panel
- InstallUtil
- MMC
- Mavinject
- Mshta
- Msiexec
- Odbcconf
- Regsvcs/Regasm
- Regsvr32
- Rundll32
- Verclsid
- System Information Discovery
- System Network Configuration Discovery
- System Network Connections Discovery
- System Script Proxy Execution
- PubPrn
- System Service Discovery
- System Services
- System Shutdown/Reboot
- Template Injection
- Traffic Signaling
- Transfer Data to Cloud Account
- Unsecured Credentials: Bash History
- Unsecured Credentials: Cloud Instance Metadata API
- Unsecured Credentials: Container API
- Use Alternate Authentication Material: Application Access Token
- User Execution
- Malicious File
- Valid Accounts
- Cloud Accounts
- Video Capture
Minor Technique changes
- Abuse Elevation Control Mechanism
- Bypass User Account Control
- Sudo and Sudo Caching
- Active Scanning
- Archive Collected Data
- Automated Exfiltration
- Traffic Duplication
- Boot or Logon Autostart Execution
- Authentication Package
- LSASS Driver
- Registry Run Keys / Startup Folder
- Time Providers
- Winlogon Helper DLL
- Boot or Logon Initialization Scripts
- Startup Items
- Browser Extensions
- Browser Session Hijacking
- Cloud Storage Object Discovery
- Command and Scripting Interpreter: AppleScript
- Command and Scripting Interpreter: Network Device CLI
- Compromise Infrastructure: Botnet
- Credentials from Password Stores
- Credentials from Web Browsers
- Password Managers
- Data from Configuration Repository
- Network Device Configuration Dump
- Data from Information Repositories
- Develop Capabilities: Malware
- Domain Trust Discovery
- Dynamic Resolution
- Domain Generation Algorithms
- Endpoint Denial of Service
- Event Triggered Execution
- Change Default File Association
- Emond
- LC_LOAD_DYLIB Addition
- Netsh Helper DLL
- Screensaver
- Windows Management Instrumentation Event Subscription
- Exfiltration Over Other Network Medium
- Exploit Public-Facing Application
- Exploitation of Remote Services
- Hide Artifacts
- Impair Defenses
- Input Capture
- Modify Authentication Process: Network Device Authentication
- Native API
- Network Denial of Service
- Non-Application Layer Protocol
- OS Credential Dumping
- Obfuscated Files or Information
- Permission Groups Discovery: Cloud Groups
- Phishing
- Phishing for Information
- Pre-OS Boot
- Process Injection
- VDSO Hijacking
- Reflective Code Loading
- Remote Services
- Scheduled Task/Job: Cron
- Shared Modules
- Software Discovery
- Stage Capabilities
- Subvert Trust Controls
- Supply Chain Compromise: Compromise Software Dependencies and Development Tools
- Supply Chain Compromise: Compromise Software Supply Chain
- System Owner/User Discovery
- Traffic Signaling: Port Knocking
- Unsecured Credentials
- Use Alternate Authentication Material
- Valid Accounts: Domain Accounts
- Windows Management Instrumentation
Technique revocations
- Boot or Logon Autostart Execution: Plist Modification (revoked by Plist File Modification (T1647))
- Scheduled Task/Job: At (Linux) (revoked by Scheduled Task/Job: At (T1053.002))
Technique deprecations
- No changes
Mobile v11.0-beta
The below changes represent the Mobile v11.0-beta release. The current production release at https://attack.mitre.org/versions/v10/matrices/mobile/ remains unchanged.
New Techniques
- Abuse Elevation Control Mechanism
- Device Administrator Permissions
- Account Access Removal
- Adversary-in-the-Middle
- Application Layer Protocol: Web Protocols
- Command and Scripting Interpreter
- Unix Shell
- Compromise Client Software Binary
- Credentials from Password Store
- Keychain
- Data Manipulation
- Transmitted Data Manipulation
- Dynamic Resolution
- Domain Generation Algorithms
- Encrypted Channel: Asymmetric Cryptography
- Encrypted Channel: Symmetric Cryptography
- Endpoint Denial of Service
- Event Triggered Execution
- Broadcast Receivers
- Execution Guardrails
- Geofencing
- Exfiltration Over Alternative Protocol
- Exfiltration Over Unencrypted Non-C2 Protocol
- Exfiltration Over C2 Channel
- Generate Traffic from Victim
- Hide Artifacts
- Suppress Application Icon
- User Evasion
- Hijack Execution Flow
- System Runtime API Hijacking
- Impair Defenses
- Device Lockout
- Disable or Modify Tools
- Prevent Application Removal
- Indicator Removal on Host
- Disguise Root/Jailbreak Indicators
- File Deletion
- Uninstall Malicious Application
- Input Capture: GUI Input Capture
- Input Capture: Keylogging
- Location Tracking: Impersonate SS7 Nodes
- Location Tracking: Remote Device Management Services
- Obfuscated Files or Information: Software Packing
- Obfuscated Files or Information: Steganography
- Out of Band Data
- Process Injection
- Ptrace System Calls
- Protected User Data
- Calendar Entries
- Call Log
- Contact List
- SMS Messages
- Software Discovery: Security Software Discovery
- Steal Application Access Token
- URI Hijacking
- Subvert Trust Controls
- Code Signing Policy Modification
- Supply Chain Compromise: Compromise Hardware Supply Chain
- Supply Chain Compromise: Compromise Software Dependencies and Development Tools
- Supply Chain Compromise: Compromise Software Supply Chain
- Virtualization/Sandbox Evasion
- System Checks
- Web Service: Bidirectional Communication
- Web Service: Dead Drop Resolver
- Web Service: One-Way Communication
Technique changes
- Access Notifications
- Application Layer Protocol
- Archive Collected Data
- Audio Capture
- Boot or Logon Initialization Scripts
- Clipboard Data
- Data Encrypted for Impact
- Data from Local System
- Download New Code at Runtime
- Drive-By Compromise
- Encrypted Channel
- Exploitation for Privilege Escalation
- Exploitation of Remote Services
- File and Directory Discovery
- Foreground Persistence
- Ingress Tool Transfer
- Input Capture
- Location Tracking
- Lockscreen Bypass
- Native API
- Network Denial of Service
- Network Service Scanning
- Non-Standard Port
- Obfuscated Files or Information
- Process Discovery
- Replication Through Removable Media
- Screen Capture
- Software Discovery
- Stored Application Data
- Supply Chain Compromise
- System Information Discovery
- System Network Configuration Discovery
- System Network Connections Discovery
- Video Capture
- Web Service
Minor Technique changes
- No changes
Technique revocations
- Access Calendar Entries (revoked by Protected User Data: Calendar Entries)
- Access Call Log (revoked by Protected User Data: Call Log)
- Access Contact List (revoked by Protected User Data: Contact List)
- Broadcast Receivers (revoked by Event Triggered Execution : Broadcast Receivers)
- Capture SMS Messages (revoked by Protected User Data: SMS Messages)
- Carrier Billing Fraud (revoked by Generate Traffic from Victim)
- Clipboard Modification (revoked by Data Manipulation: Transmitted Data Manipulation)
- Code Injection (revoked by Process Injection: Ptrace System Calls)
- Command-Line Interface (revoked by Command and Scripting Interpreter: Unix Shell)
- Delete Device Data (revoked by Indicator Removal on Host: File Deletion)
- Device Administrator Permissions (revoked by Abuse Elevation Control Mechanism: Device Administrator Permissions)
- Device Lockout (revoked by Impair Defenses: Device Lockout)
- Disguise Root/Jailbreak Indicators (revoked by Indicator Removal on Host: Disguise Root/Jailbreak Indicators)
- Domain Generation Algorithms (revoked by Dynamic Resolution: Domain Generation Algorithms)
- Downgrade to Insecure Protocols (revoked by Adversary-in-the-Middle)
- Eavesdrop on Insecure Network Communication (revoked by Adversary-in-the-Middle)
- Evade Analysis Environment (revoked by Virtualization/Sandbox Evasion: System Checks)
- Exfiltration Over Other Network Medium (revoked by Out of Band Data)
- Exploit SS7 to Track Device Location (revoked by Location Tracking: Impersonate SS7 Nodes)
- Generate Fraudulent Advertising Revenue (revoked by Generate Traffic from Victim)
- Geofencing (revoked by Execution Guardrails: Geofencing)
- Input Prompt (revoked by Input Capture: GUI Input Capture)
- Install Insecure or Malicious Configuration (revoked by Subvert Trust Controls: Code Signing Policy Modification)
- Keychain (revoked by Credentials from Password Store: Keychain)
- Manipulate App Store Rankings or Ratings (revoked by Generate Traffic from Victim)
- Manipulate Device Communication (revoked by Adversary-in-the-Middle)
- Modify System Partition (revoked by Hijack Execution Flow: System Runtime API Hijacking)
- Network Information Discovery (revoked by System Network Connections Discovery)
- Network Traffic Capture or Redirection (revoked by Adversary-in-the-Middle)
- Remotely Track Device Without Authorization (revoked by Location Tracking: Remote Device Management Services)
- Rogue Cellular Base Station (revoked by Adversary-in-the-Middle)
- Rogue Wi-Fi Access Points (revoked by Adversary-in-the-Middle)
- Suppress Application Icon (revoked by Hide Artifacts: Suppress Application Icon)
- URI Hijacking (revoked by Steal Application Access Token: URI Hijacking)
- Uninstall Malicious Application (revoked by Indicator Removal on Host: Uninstall Malicious Application)
- User Evasion (revoked by Hide Artifacts: User Evasion)
Technique deprecations
- Access Sensitive Data in Device Logs
- Attack PC via USB Connection
- Commonly Used Port
- Deliver Malicious App via Authorized App Store
- Deliver Malicious App via Other Means
- Exploit SS7 to Redirect Phone Calls/SMS
- Exploit TEE Vulnerability
- Exploit via Radio Interfaces
- Masquerade as Legitimate Application
- Modify Cached Executable Code
- Modify Trusted Execution Environment
- Obtain Device Cloud Backups
- Remotely Wipe Data Without Authorization
- SIM Card Swap
Software
Enterprise
New Software
- AADInternals
- CaddyWiper
- CharmPower
- Chrommme
- Clambling
- Cyclops Blink
- DRATzarus
- DarkWatchman
- Diavol
- Donut
- Ferocious
- Flagpro
- FoggyWeb
- Gelsemium
- Green Lambert
- HermeticWiper
- HermeticWizard
- KOCTOPUS
- LitePower
- Lizar
- Meteor
- Mythic
- Neoichor
- Pandora
- Peirates
- PowerPunch
- QuietSieve
- RCSession
- ROADTools
- SILENTTRINITY
- SysUpdate
- ThreatNeedle
- TinyTurla
- Tomiris
- Torisma
- TrailBlazer
- WarzoneRAT
- WhisperGate
- Zox
Software changes
- AppleSeed
- Arp
- Backdoor.Oldrea
- Bisonal
- BloodHound
- Brave Prince
- CHOPSTICK
- Cobalt Strike
- Conti
- Derusbi
- EKANS
- Empire
- FinFisher
- Gold Dragon
- GoldMax
- Hikit
- Hydraq
- HyperBro
- InvisiMole
- KONNI
- KillDisk
- Koadic
- LockerGoga
- Mimikatz
- Ngrok
- OSX_OCEANLOTUS.D
- Orz
- PLEAD
- Ping
- PlugX
- PoetRAT
- PoisonIvy
- Prikormka
- Pteranodon
- QuasarRAT
- REvil
- ROKRAT
- Remcos
- Responder
- Ryuk
- SUNBURST
- SombRAT
- Stuxnet
- ThiefQuest
- Trojan.Karagany
- USBStealer
- Waterbear
- Winnti for Windows
- XCSSET
- ZxShell
- at
- ftp
- gh0st RAT
- njRAT
- route
- schtasks
Minor Software changes
- Anchor
- BoomBox
- Bundlore
- China Chopper
- EVILNUM
- Industroyer
- Maze
- Mis-Type
- Misdat
- Nidiran
- Octopus
- S-Type
- SYNful Knock
- TSCookie
- WindTail
- ZLib
Software revocations
- No changes
Software deprecations
- No changes
Mobile
New Software
- No changes
Software changes
Minor Software changes
Software revocations
- No changes
Software deprecations
- No changes
Groups
Enterprise
New Groups
Group changes
- APT28
- APT29
- Axiom
- BlackTech
- Dragonfly
- FIN7
- Gamaredon Group
- HAFNIUM
- Indrik Spider
- Ke3chang
- Kimsuky
- Lazarus Group
- Magic Hound
- Mustang Panda
- Sandworm Team
- TeamTNT
- Threat Group-3390
- Tonto Team
- Turla
- Volatile Cedar
- WIRTE
- Winnti Group
Minor Group changes
Group revocations
- Dragonfly 2.0 (revoked by Dragonfly)
Group deprecations
- No changes
Mobile
New Groups
- No changes
Group changes
Minor Group changes
- No changes
Group revocations
- No changes
Group deprecations
- No changes
Mitigations
Enterprise
New Mitigations
- No changes
Mitigation changes
Minor Mitigation changes
- No changes
Mitigation revocations
- No changes
Mitigation deprecations
- No changes
Mobile
New Mitigations
- No changes
Mitigation changes
- No changes
Minor Mitigation changes
- No changes
Mitigation revocations
- No changes
Mitigation deprecations
Data Sources and/or Components
Enterprise
New Data Sources and/or Components
- No changes
Data Source and/or Component changes:
- No changes
Minor Data Source and/or Component changes
- Active Directory
- Application Log
- Cloud Service
- Command
- Domain Name: Active DNS
- Drive
- Driver
- File
- File Deletion
- Firewall
- Firmware
- Group
- Logon Session
- Malware Repository: Malware Content
- Malware Repository: Malware Metadata
- Module
- Named Pipe
- Network Share
- Network Traffic
- Network Connection Creation
- Process
- OS API Execution
- Scheduled Job
- Sensor Health
- Host Status
- Service
- User Account
- Volume
- Web Credential
Data Source and/or Component revocations
- No changes
Data Source and/or Component deprecations
- No changes
Mobile
ATT&CK for Mobile does not support data sources
Contributors to this release
- Abhijit Mohanta, @abhijit_mohanta, Uptycs
- Akshat Pradhan, Qualys
- Alex Hinchliffe, Palo Alto Networks
- Alex Parsons, Crowdstrike
- Alex Spivakovsky, Pentera
- Andrew Northern, @ex_raritas
- Antonio Piazza, @antman1p
- Austin Clark, @c2defense
- Bryan Campbell, @bry_campbell
- Chris Romano, Crowdstrike
- Clément Notin, Tenable
- Cody Thomas, SpecterOps
- Craig Smith, BT Security
- Csaba Fitzl @theevilbit of Offensive Security
- Daniel Acevedo, Blackbot
- Daniel Feichter, @VirtualAllocEx, Infosec Tirol
- Daniyal Naeem, BT Security
- Darin Smith, Cisco
- Dror Alon, Palo Alto Networks
- Edward Millington
- Elvis Veliz, Citi
- Emily Ratliff, IBM
- Eric Kaiser @ideologysec
- ESET
- Hannah Simes, BT Security
- Harshal Tupsamudre, Qualys
- Hiroki Nagahama, NEC Corporation
- Isif Ibrahima, Mandiant
- James_inthe_box, Me
- Jan Petrov, Citi
- Jannie Li, Microsoft Threat Intelligence Center (MSTIC)
- Jen Burns, HubSpot
- Jeremy Galloway
- Joas Antonio dos Santos, @C0d3Cr4zy, Inmetrics
- John Page (aka hyp3rlinx), ApparitionSec
- Jon Sternstein, Stern Security
- Kobi Haimovich, CardinalOps
- Krishnan Subramanian, @krish203
- Kyaw Pyiyt Htet, @KyawPyiytHtet
- Leo Zhang, Trend Micro
- Manikantan Srinivasan, NEC Corporation India
- Massimiliano Romano, BT Security
- Matthew Green
- Mayan Arora aka Mayan Mohan
- Mayuresh Dani, Qualys
- Michael Raggi @aRtAGGI
- Mohamed Kmal
- NEC
- NST Assure Research Team, NetSentries Technologies
- Oleg Kolesnikov, Securonix
- Or Kliger, Palo Alto Networks
- Pawel Partyka, Microsoft 365 Defender
- Phil Taylor, BT Security
- Pià Consigny, Tenable
- Pooja Natarajan, NEC Corporation India
- Praetorian
- Prasad Somasamudram, McAfee
- Ram Pliskin, Microsoft Azure Security Center
- Richard Julian, Citi
- Runa Sandvik
- Sekhar Sarukkai, McAfee
- Selena Larson, @selenalarson
- Shilpesh Trivedi, Uptycs
- Sittikorn Sangrattanapitak
- Steven Du, Trend Micro
- Suzy Schapperle – Microsoft Azure Red Team
- Syed Ummar Farooqh, McAfee
- Taewoo Lee, KISA
- The Wover, @TheRealWover
- Tiago Faria, 3CORESec
- Tony Lee
- Travis Smith, Qualys
- TruKno
- Tsubasa Matsuda, NEC Corporation
- Vinay Pidathala
- Wes Hurd
- Wietze Beukema, @wietze
- Wojciech Lesicki
- Zachary Abzug, @ZackDoesML
- Zachary Stanford, @svch0st