BIAS: Bluetooth Impersonation AttackS
Daniele Antonioli (Postdoc at the EPFL Cyber-Physical Systems Security, Network Security, Wireless Security, Embedded Systems Security, Applied Cryptography, SoCurity) , Kasper Rasmussen (Faculty Security of Wireless Networks, Protocol design, Applied Cryptography, Security of embedded systems, Cyber-physical systems), and Nils Ole Tippenhauer (Faculty Security of Cyber-Physical Systems, Security of Physical-Layer Wireless, IoT Security) Researchers at the École Polytechnique Fédérale de Lausanne (EPFL) have identified a security vulnerability related to pairing in Bluetooth BR/EDR connections. The Bluetooth Special Interest Group (SIG) has been forced to update its specification after academics disclosed the vulnerability in the way connections are made between devices using BR/EDR. This configuration is also known as Bluetooth Classic. The researchers identified that it is possible for an attacking device spoofing the address of a previously bonded remote device to complete the authentication procedure with some paired/bonded devices while not possessing the link key. This may permit an attacker to negotiate a reduced encryption key strength with a device that is still vulnerable to the Key Negotiation of Bluetooth attack disclosed in 2019. If the encryption key length reduction is successful, an attacker may be able to brute force the encryption key and spoof the remote paired device. If the encryption key length reduction is unsuccessful, the attacker will not be able to establish an encrypted link but may still appear authenticated to the host.
For this attack to be successful, an attacking device would need to be within the wireless range of a vulnerable Bluetooth device that has previously established a BR/EDR bonding with a remote device with a Bluetooth address known to the attacker. For devices supporting Secure Connections mode, the attacker claims to be the previously paired remote device but with no support for Secure Connections. This will generally permit the attacker to proceed with an attack on legacy authentication unless the device is in Secure Connections Only mode. If the attacker can either downgrade authentication in this manner or is attacking a device that does not support Secure Connections, the attacker initiates a master-slave role switch to place itself into the master role and become the authentication initiator. If successful, it completes authentication with the attacked device. If the attacked device does not mutually authenticate with the attacker in the master role, this will result in an authentication-complete notification even though the attacker does not possess the link key.

Researcher Uwach ~
“About the BIAS attack
TL;DR: The Bluetooth standard provides authentication mechanisms based on a long term pairing key, which are designed to protect against impersonation attacks. The BIAS attacks from our new paper demonstrate that those mechanisms are broken, and that an attacker can exploit them to impersonate any Bluetooth master or slave device. Our attacks are standard-compliant, and can be combined with other attacks, including the KNOB attack. In the paper, we also describe a low cost implementation of the attacks and our evaluation results on 30 unique Bluetooth devices using 28 unique Bluetooth chips.”
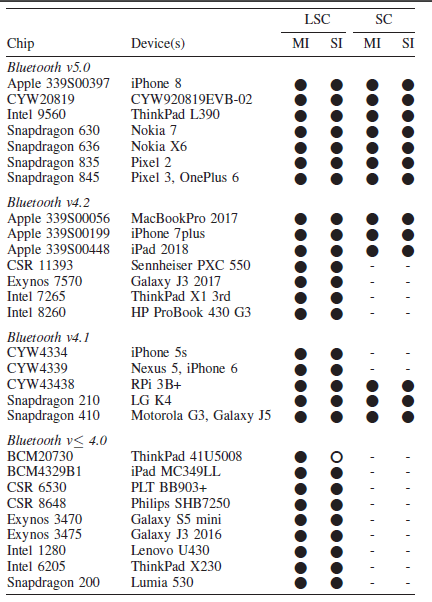
Affected Devices include and not limited to Apple 339S00397 iPhone 8 ,CYW20819 CYW920819EVB-02 ,Intel 9560 ThinkPad L390 ,Snapdragon 630 Nokia 7 ,Snapdragon 636 Nokia X6 ,Snapdragon 835 Pixel 2 ,Snapdragon 845 Pixel 3, OnePlus 6, Apple 339S00056 MacBookPro 2017 ,Apple 339S00199 iPhone 7plus ,Apple 339S00448 iPad 2018 ,CSR 11393 Sennheiser PXC 550 ,Exynos 7570 Galaxy J3 2017,Intel 7265 ThinkPad X1 3rd ,Intel 8260 HP ProBook 430 G3 ,CYW4334 iPhone 5s ,CYW4339 Nexus 5, iPhone 6 ,CYW43438 RPi 3B+ ,Snapdragon 210 LG K4 ,Snapdragon 410 Motorola G3, Galaxy J5 ,BCM20730 ThinkPad 41U5008 ,BCM4329B1 iPad MC349LL ,CSR 6530 PLT BB903+ ,CSR 8648 Philips SHB7250 ,Exynos 3470 Galaxy S5 mini ,Exynos 3475 Galaxy J3 2016 ,Intel 1280 Lenovo U430 ,Intel 6205 ThinkPad X230 ,Snapdragon 200 Lumia 530.
Details
Bluetooth Classic (also called Bluetooth BR/EDR) is a wireless communication protocol commonly used between low power devices to transfer data, e.g., between a wireless headset and a phone, or between two laptops. Bluetooth communications might contain private and/or sensitive data, and the Bluetooth standard provides security features to protect against someone who wants to eavesdrop and/or manipulate your information. We found and exploited a severe vulnerability in the Bluetooth BR/EDR specification that allows an attacker to break the security mechanisms of Bluetooth for any standard-compliant device. As a result, an attacker can impersonate a device towards the host after both have previously been successfully paired in the absence of the attacker.
We call our attack Bluetooth Impersonation AttackS (BIAS). Because this attack affects basically all devices that “speak Bluetooth”, we performed a responsible disclosure with the Bluetooth Special Interest Group (Bluetooth SIG) – the standards organisation that oversees the development of Bluetooth standards – in December 2019 to ensure that workarounds could be put in place.
Are My Devices Vulnerable?
The BIAS attack is possible due to flaws in the Bluetooth specification. As such, any standard-compliant Bluetooth device can be expected to be vulnerable. We conducted BIAS attacks on more than 28 unique Bluetooth chips (by attacking 30 different devices). At the time of writing, we were able to test chips from Cypress, Qualcomm, Apple, Intel, Samsung and CSR. All devices that we tested were vulnerable to the BIAS attack.
After we disclosed our attack to industry in December 2019, some vendors might have implemented workarounds for the vulnerability on their devices. So the short answer is: if your device was not updated after December 2019, it is likely vulnerable. Devices updated afterwards might be fixed.
Bluetooth Uwach ~
To remedy this vulnerability, the Bluetooth SIG is updating the Bluetooth Core Specification to clarify when role switches are permitted, to require mutual authentication in legacy authentication and to recommend checks for encryption-type to avoid a downgrade of secure connections to legacy encryption. These changes will be introduced into a future specification revision.
Until this occurs, the Bluetooth SIG is strongly recommending that vendors ensure that reduction of the encryption key length below 7 octets is not permitted, that hosts initiate mutual authentication when performing legacy authentication, that hosts support Secure Connections Only mode when this is possible, and that the Bluetooth authentication not be used to independently signal a change in device trust without first requiring the establishment of an encrypted link.
The Bluetooth SIG is also broadly communicating details on this vulnerability and its remedies to our member companies and is encouraging them to rapidly integrate any necessary patches. As always, Bluetooth users should ensure they have installed the latest recommended updates from device and operating system manufacturers.