MITRE ATT&CK® Released Updates in April 2021 With Additional Techniques and Structuring
MITRE ATT&CK® is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
With the creation of ATT&CK, MITRE is fulfilling its mission to solve problems for a safer world — by bringing communities together to develop more effective cybersecurity. ATT&CK is open and available to any person or organization for use at no charge.
MITRE ATT&CK® Released Updates in April 2021 With Additional Techniques and Structuring update versioned as ATT&CK v9. “The April 2021 (v9) ATT&CK release updates Techniques, Groups, and Software for Enterprise, Mobile, and ICS. The biggest changes are a change in how we describe data sources, the addition of the Containers and Google Workspace platforms, and the replacement of the AWS, GCP, and Azure platforms with a single IaaS (Infrastructure as a Service) platform. An accompanying blog post describes these changes and additions in more detail, with a focus on the new structure of data sources.” As stated by MITRE.

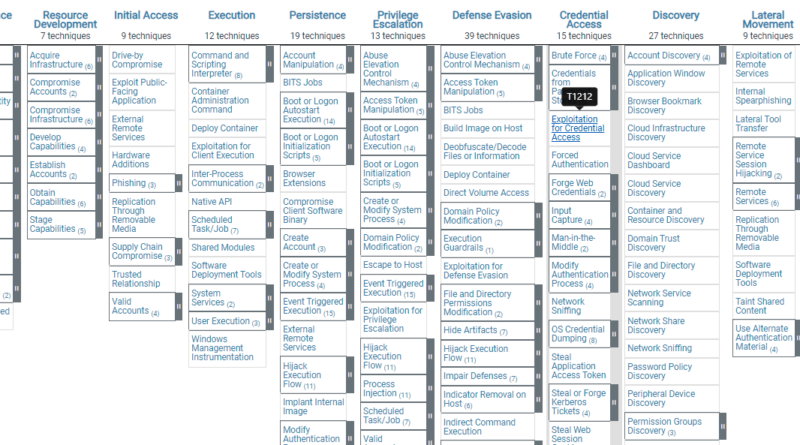
This version of ATT&CK for Enterprise contains 14 Tactics, 185 Techniques, and 367 Sub-techniques.
Techniques
Enterprise
New Techniques:
- Boot or Logon Autostart Execution: Active Setup
- Boot or Logon Autostart Execution: XDG Autostart Entries
- Build Image on Host
- Container Administration Command
- Container and Resource Discovery
- Credentials from Password Stores: Password Managers
- Credentials from Password Stores: Windows Credential Manager
- Deploy Container
- Escape to Host
- Scheduled Task/Job: Container Orchestration Job
- Stage Capabilities
- Subvert Trust Controls: Code Signing Policy Modification
- Subvert Trust Controls: Mark-of-the-Web Bypass
- System Location Discovery
- System Network Configuration Discovery: Internet Connection Discovery
- Unsecured Credentials: Container API
- User Execution: Malicious Image
Technique changes:
- Account Discovery
- Account Manipulation
- BITS Jobs
- Boot or Logon Autostart Execution: Kernel Modules and Extensions
- Boot or Logon Autostart Execution: Shortcut Modification
- Boot or Logon Initialization Scripts: RC Scripts
- Browser Extensions
- Brute Force
- Cloud Infrastructure Discovery
- Cloud Service Dashboard
- Cloud Service Discovery
- Command and Scripting Interpreter: JavaScript
- Command and Scripting Interpreter: Windows Command Shell
- Create Account
- Credentials from Password Stores: Credentials from Web Browsers
- Data Destruction
- Data Encrypted for Impact
- Data Staged
- Data from Cloud Storage Object
- Data from Information Repositories
- Defacement
- Develop Capabilities: Digital Certificates
- Develop Capabilities: Malware
- Email Collection
- Endpoint Denial of Service
- Establish Accounts
- Event Triggered Execution: Unix Shell Configuration Modification
- Event Triggered Execution: Windows Management Instrumentation Event Subscription
- Exploit Public-Facing Application
- Exploitation for Privilege Escalation
- External Remote Services
- Forge Web Credentials
- Hijack Execution Flow
- Impair Defenses
- Implant Internal Image
- Indicator Removal on Host
- Internal Spearphishing
- Masquerading
- Modify Authentication Process
- Modify Cloud Compute Infrastructure
- Network Denial of Service
- Network Service Scanning
- Network Sniffing
- Obtain Capabilities: Digital Certificates
- Permission Groups Discovery
- Phishing
- Phishing for Information
- Remote System Discovery
- Resource Hijacking
- Scheduled Task/Job
- Service Stop
- Signed Binary Proxy Execution: Msiexec
- Software Discovery
- Steal Application Access Token
- Steal Web Session Cookie
- Steal or Forge Kerberos Tickets
- System Information Discovery
- System Network Connections Discovery
- System Time Discovery
- Traffic Signaling
- Transfer Data to Cloud Account
- Trusted Developer Utilities Proxy Execution: MSBuild
- Trusted Relationship
- Unsecured Credentials
- Unused/Unsupported Cloud Regions
- Use Alternate Authentication Material
- User Execution
- Valid Accounts
- Virtualization/Sandbox Evasion: System Checks
- Virtualization/Sandbox Evasion: Time Based Evasion
Minor Technique changes:
- Access Token Manipulation
- Acquire Infrastructure
- Active Scanning
- Automated Exfiltration
- Boot or Logon Autostart Execution
- Boot or Logon Initialization Scripts
- Command and Scripting Interpreter
- Compromise Accounts
- Compromise Infrastructure
- Credentials from Password Stores
- Data Manipulation
- Develop Capabilities
- Direct Volume Access
- Domain Policy Modification
- Dynamic Resolution: Domain Generation Algorithms
- Encrypted Channel
- Establish Accounts: Email Accounts
- Establish Accounts: Social Media Accounts
- Event Triggered Execution
- Execution Guardrails: Environmental Keying
- Exploitation of Remote Services
- Gather Victim Host Information
- Gather Victim Identity Information
- Gather Victim Network Information
- Gather Victim Org Information
- Hardware Additions
- Impair Defenses: Impair Command History Logging
- Impair Defenses: Indicator Blocking
- Indicator Removal on Host: Network Share Connection Removal
- Input Capture: Credential API Hooking
- Man in the Browser
- Man-in-the-Middle: ARP Cache Poisoning
- Masquerading: Masquerade Task or Service
- Masquerading: Rename System Utilities
- Network Share Discovery
- OS Credential Dumping
- Obfuscated Files or Information
- Obtain Capabilities
- Phishing for Information: Spearphishing Service
- Process Injection
- Rogue Domain Controller
- Scheduled Task/Job: Scheduled Task
- Search Closed Sources
- Search Open Technical Databases
- Search Open Websites/Domains
- Search Victim-Owned Websites
- Signed Binary Proxy Execution
- Software Deployment Tools
- Subvert Trust Controls
- Supply Chain Compromise
- System Network Configuration Discovery
- Trusted Developer Utilities Proxy Execution
- Virtualization/Sandbox Evasion
- XSL Script Processing
Technique revocations: No changes
Technique deprecations: No changes
Mobile
New Techniques:
Technique changes:
Minor Technique changes:
Technique revocations: No changes
Technique deprecations: No changes
Software
Enterprise
New Software:
- AppleJeus
- BLINDINGCAN
- Bazar
- BendyBear
- BitPaymer
- BlackMould
- CSPY Downloader
- Caterpillar WebShell
- ConnectWise
- Conti
- Crutch
- Doki
- DropBook
- Dtrack
- ECCENTRICBANDWAGON
- EVILNUM
- Egregor
- Explosive
- GoldFinder
- GoldMax
- Grandoreiro
- GuLoader
- Hildegard
- HyperStack
- IronNetInjector
- Javali
- KGH_SPY
- Kerrdown
- Kinsing
- LookBack
- Lucifer
- MegaCortex
- Melcoz
- MoleNet
- NBTscan
- Out1
- P.A.S. Webshell
- Pay2Key
- Penquin
- Pysa
- RemoteUtilities
- SLOTHFULMEDIA
- SUPERNOVA
- ShadowPad
- SharpStage
- Sibot
- Spark
- TAINTEDSCRIBE
- ThiefQuest
- Waterbear
Software changes:
- Agent Tesla
- Astaroth
- BabyShark
- BlackEnergy
- Carbon
- China Chopper
- Cobalt Strike
- ComRAT
- Ebury
- Empire
- EvilBunny
- Exaramel for Linux
- FALLCHILL
- Fysbis
- Gazer
- HTRAN
- HiddenWasp
- Hikit
- Kazuar
- LaZagne
- Machete
- Matryoshka
- Mimikatz
- More_eggs
- NETWIRE
- Net
- NotPetya
- OSX_OCEANLOTUS.D
- Olympic Destroyer
- PoetRAT
- PoisonIvy
- PowerSploit
- Proton
- REvil
- ROKRAT
- Ragnar Locker
- Raindrop
- Ramsay
- Ryuk
- SDBbot
- SEASHARPEE
- SUNBURST
- SUNSPOT
- TEARDROP
- TrickBot
- Ursnif
- Valak
- Zebrocy
- gh0st RAT
Minor Software changes:
- BONDUPDATER
- BOOTRASH
- Briba
- Carbanak
- Catchamas
- DustySky
- Emotet
- HAMMERTOSS
- Hi-Zor
- Hydraq
- KeyBoy
- Linfo
- Linux Rabbit
- Naid
- Nerex
- Net Crawler
- Orz
- PUNCHBUGGY
- Pasam
- PoshC2
- PowerStallion
- ROCKBOOT
- Reaver
- SeaDuke
- Shamoon
- TURNEDUP
- TinyZBot
- Vasport
- WellMess
- Wiarp
- jRAT
- meek
- spwebmember
Software revocations: No changes
Software deprecations: No changes
Mobile
New Software:
- Android/AdDisplay.Ashas
- AndroidOS/MalLocker.B
- Asacub
- CHEMISTGAMES
- CarbonSteal
- Circles
- DoubleAgent
- Exobot
- FrozenCell
- GPlayed
- Golden Cup
- GoldenEagle
- HenBox
- Red Alert 2.0
- SilkBean
- TERRACOTTA
- Tiktok Pro
Software changes:
Minor Software changes: No changes
Software revocations: No changes
Software deprecations: No changes
Groups
Enterprise
New Groups:
- Ajax Security Team
- Bouncing Golf
- Evilnum
- Fox Kitten
- HAFNIUM
- Higaisa
- Indrik Spider
- Mustang Panda
- Operation Wocao
- Sidewinder
- Silent Librarian
- TA551
- Volatile Cedar
- Windigo
- ZIRCONIUM
Group changes:
- APT28
- APT29
- APT32
- APT39
- APT41
- BRONZE BUTLER
- BlackTech
- Carbanak
- Chimera
- Cobalt Group
- CopyKittens
- Darkhotel
- Dragonfly 2.0
- Elderwood
- FIN6
- GALLIUM
- GOLD SOUTHFIELD
- Kimsuky
- Lazarus Group
- Machete
- Magic Hound
- Molerats
- MuddyWater
- OilRig
- PLATINUM
- Sandworm Team
- Silence
- Stealth Falcon
- TA505
- Threat Group-3390
- Tropic Trooper
- Turla
- Windshift
- Wizard Spider
- menuPass
Minor Group changes:
Group revocations:
- UNC2452 (revoked by APT29)
Group deprecations: No changes
Group deletions:
- Charming Kitten
Mobile
New Groups:
Group changes:
Minor Group changes: No changes
Group revocations: No changes
Group deprecations: No changes
Mitigations
Enterprise
New Mitigations: No changes
Mitigation changes: No changes
Minor Mitigation changes:
Mitigation revocations: No changes
Mitigation deprecations: No changes
Mitigation deletions:
- Group Policy Modification Mitigation
Mobile
New Mitigations: No changes
Mitigation changes: No changes
Minor Mitigation changes:
Mitigation revocations: No changes
Mitigation deprecations: No changes
Resources: