Gartner EDRs are not perfect, fail against common attacks
Advanced Persistent threats have been a pain for blue teams for a very long time, and one of the key tool in the arsenal is Endpoint Detection and Response tools since the recent past, however, they come with their limitations as well. endpoint detection & response (EDR) software from 18 of today’s top cybersecurity firms was tested by a Department of Informatics, University of Piraeus, Piraeus, Greece and Information Management Systems Institute, Athena Research Center, Marousi, Greece, and found that many fail to detect some of the most common attack techniques used by advanced persistent threat actors, such as state-sponsored espionage groups and ransomware gangs based on which a research paper was published by George Karantzas and Constantinos Patsakis in Journal of Cybersecurity and Privacy by name An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors.1 as per them:
“Our results indicate that there is still a lot of room for improvement as state-of-the-art EDRs fail to prevent and log the bulk of the attacks that are reported in this work,”
In an Era of Constantly Evolving Threat Landscape and sophistication and scale of Cyberattacks to such an extent that even the World Economic Forum considers it the second most threatening risk for global commerce over the next decade2. and the Underground market is run by individuals, Organizations by nation state actors has grown multifold. instead of regular trivial Cyber Attacks today we are witnessing Advanced Persistent threats APT’s, In Trivial attacks which are a major part of cyber-attacks even today attackers are usually looking for low hanging fruits and try to monetize the target ASAP by exploiting easier compromise methods, where were APT’s actors try to remain undetected for prolonged persistence and exploit complex and lesser exploited mechanisms.
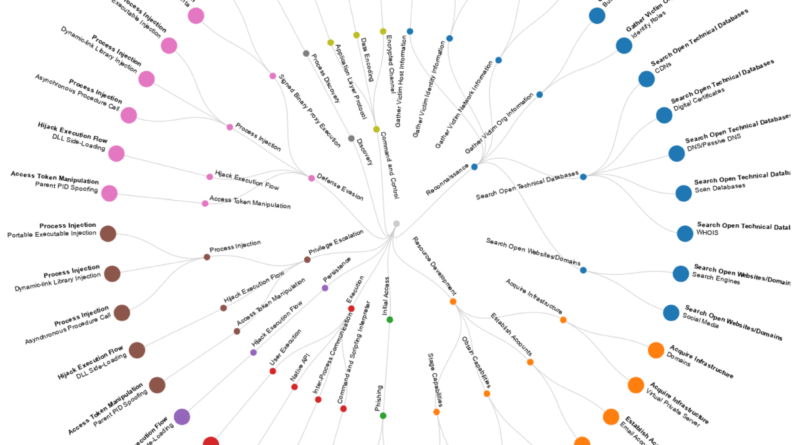
They have Used the ATT&CK Knowledge base and model to test these EDR’s:

EDR’s Were selected based on Gartner 2021 report
The attack vectors are the following:
A .cpl file: https://github.com/rvrsh3ll/CPLResourceRunner
A legitimate Microsoft (MS) Teams installation https://attack.mitre.org/techniques/T1574/002/ https://github.com/slaeryan/AQUARMOURY
An unsigned PE executable file;
An HTA file. https://github.com/med0x2e/GadgetToJScript
EDR’s In Scope
Carbon Black, CrowdStrike Falcon, ESET PROTECT Enterprise, F-Secure Elements Endpoint Detection and Response, Kaspersky Endpoint Detection and Response-KEDR, McAfee Endpoint Protection, Sentinel One, Sophos Intercept X with EDR, Symantec Endpoint Protection, Trend Micro Apex One, Windows Defender for Endpoints (ATP)
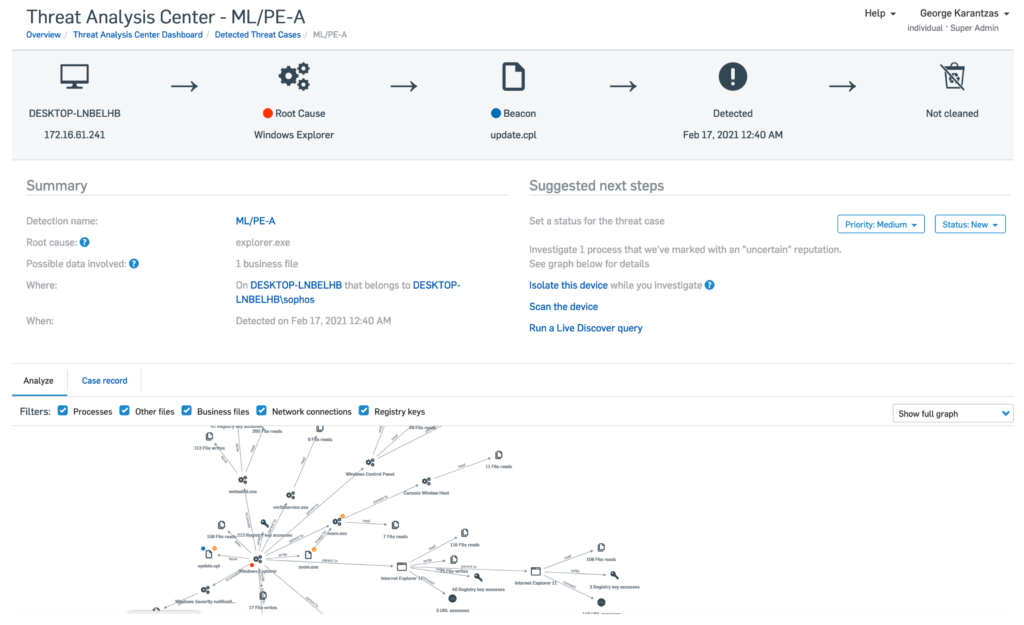
Apart from Bypassing they also tried Tampering with Telemetry of them.
and came up with the following results:

Results of these tests showcased that no EDRs had full coverage for all attack vectors, allowing attackers to execute via the attack chain and get further access.
As per the tests conducted on telemetry research team puts a case that this brings forth a scenario where the attackers could turn them off or disable their telemetry functions, But not all EDRs were tested part of this experiment.