Indian Organizations also targetted by Bvp47 backdoor of US NSA Equation Group
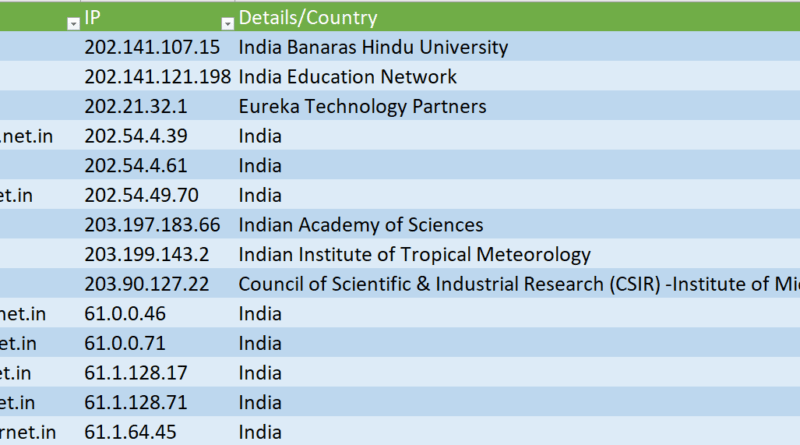
Banaras Hindu University, India Education Network, Eureka Technology Partners, Indian Academy of Sciences, Indian Institute of Tropical Meteorology, Council of Scientific & Industrial Research (CSIR) – Institute of Microbial Technology (IMTech) and other Indian Organizations were targetted by US NSA Equation Group as per the research of Pangu Lab, It focuses on advanced security research and attack-defense confrontation research. It has solid research capabilities in operating systems, virtualization, the Internet of Things, and application security research. and experience.
| S.No | Domain Name | IP | Details/Country |
| 1 | mail.bhu.ac.in | 202.141.107.15 | India Banaras Hindu University |
| 2 | mtccsun.imtech.ernet.in | 202.141.121.198 | India Education Network |
| 3 | axil.eureka.lk | 202.21.32.1 | Eureka Technology Partners |
| 4 | mu-me01-ns-ctm001.vsnl.net.in | 202.54.4.39 | India |
| 5 | vsn1radius1.vsn1.net.in | 202.54.4.61 | India |
| 6 | vsnl-navis.emc-sec.vsnl.net.in | 202.54.49.70 | India |
| 7 | ns1.ias.ac.in | 203.197.183.66 | Indian Academy of Sciences |
| 8 | mail.tropmet.res.in | 203.199.143.2 | Indian Institute of Tropical Meteorology |
| 9 | mail1.imtech.res.in | 203.90.127.22 | Council of Scientific & Industrial Research (CSIR) -Institute of Microbial Technology (IMTech) |
| 10 | nd11mx1-a-fixed.sancharnet.in | 61.0.0.46 | India |
| 11 | ndl1pp1-a-fixed.sancharnet.in | 61.0.0.71 | India |
| 12 | bgl1dr1-a-fixed.sancharnet.in | 61.1.128.17 | India |
| 13 | bgl1pp1-a-fixed.sancharnet.in | 61.1.128.71 | India |
| 14 | mum1mr1-a-fixed.sancharnet.in | 61.1.64.45 | India |
Researchers from the Pangu Lab extracted a set of advanced backdoors on the Linux platform in a specific month of 2013, during an in-depth forensic investigation of a host in a key domestic department. The backdoors used advanced covert channel behaviour based on TCP SYN packets, code obfuscation, system hiding, and self-destruction design. In the event that the backdoor is unable to fully decrypt, it is discovered that it requires the check code bound to the host in order to function normally. The researchers then successfully ran the backdoor after cracking the check code. This appears to be a top-tier APT backdoor based on some behavioural functions, but further investigation requires the attacker’s asymmetric encrypted private key to activate the remote control function.

The team named the corresponding malicious code “Bvp47” at the time, based on the most common string “Bvp” in the sample and the numerical value 0x47 used in the encryption algorithm.
Two batches of hacking files purportedly used by “The Equation Group” were published by “The Shadow Brokers” in 2016 and 2017. Researchers from Pangu Lab discovered the private key that can be used to remotely trigger the backdoor Bvp47 in these hacking files. As a result, Bvp47 can be classified as a hacker tool belonging to “The Equation Group.”

Further investigation revealed that the multiple procedures and attack operation manuals revealed by “The Shadow Broker” are identical to the only identifier used in the NSA network attack platform operation manual [References 3 and 4] exposed by CIA analyst Snowden in the “Prism” incident in 2013.
Given the US government’s prosecution of Edward Snowden on three counts of “spreading national defense information without permission and deliberately spreading confidential information” it can be concluded that the documents published by “The Shadow Brokers” are indeed NSA, proving that “The Equation Group” is NSA’s top-tier backdoor. Aside from that, “The Shadow Brokers” files revealed that there were 287 targets in 45 countries, including Russia, Japan, Spain, Germany, Italy, and others. The assault lasted more than a decade. Furthermore, one Japanese victim is being used as a jump server for future attacks.
For several Bvp47 incidents, Pangu Lab has a code called “Operation Telescreen.” In his novel “1984”, British writer George Orwell imagines a device called a telescreen. It can be used to remotely monitor the person or organisation that deploys the telescreen, and the “thought police” can monitor any telescreen’s information and behaviour at will.

The Equation Group is the world’s most powerful cyber-attack group, and it is widely believed to be linked to the US National Security Agency. Equation group is a first-class hacking group, based on the attack tools associated with the organisation, including Bvp47. The programme is well-designed, powerful, and adaptable. Its network attack capability, which relied on zero-day vulnerabilities, was unstoppable, and it acquired data under covert control with ease. In national-level cyberspace conflict, the Equation Group holds a commanding position.
Complete report English version can be read from here.
It is interesting to see that most media houses in India are silent on these hacking attempts on Indian organizations. though we have little expectation from Indian media and even less from the Indian Government regarding whether it will be raised to US Ambassador to India or any clarification will be sought from him or not will be the thing to see.