NATO Examines Data Breach from Missile Vendor on the Dark Web
One set of documents purportedly belonging to an EU defense supplier includes information on the weapons Ukraine used to fight Russia.
According to a report in the media, NATO is looking into the leak of data that hackers are said to have purchased on the Dark Web from a European missile systems company.
The stolen information contains blueprints for the weapons that Ukraine has been using to fight Russia right now.
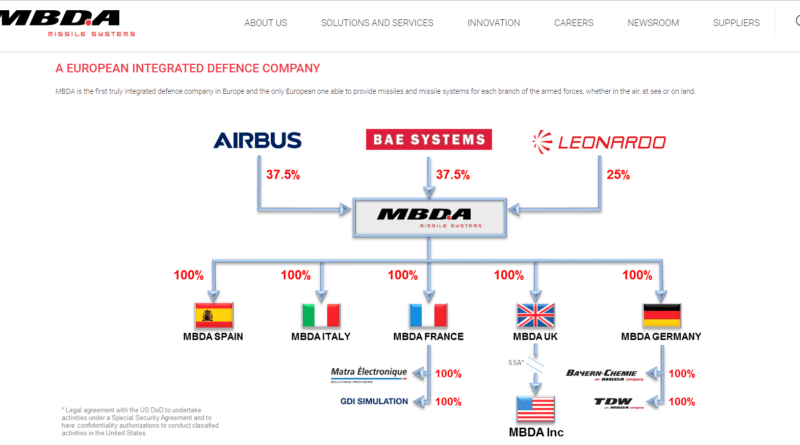
The French-based integrated defence company MBDA Missile Systems has admitted that information from its systems is included in the cache being sold by threat actors on hacker forums following what appears to be a ransomware attack.
Nothing being offered for sale is classified information, despite what the cyberattackers claimed in their ads, according to MBDA. Additionally, the company’s internal networks were not used to obtain the data; rather, it came from a compromised external hard drive.
A NATO official told Dark Reading on Monday that NATO is “assessing claims relating to data allegedly stolen from MBDA”
The officials said, “We have no indication that any NATO network has been compromised.”
Multiple Extortions
In a post on its website at the beginning of August, MBDA acknowledged that it had been “the subject of a blackmail attempt by a criminal group that falsely claims to have hacked the company’s information networks.”

The post claims that because the company declined to pay the ransom, the data was released for online sale.
According to a report from the BBC, which first reported on the NATO investigation on Friday, threat actors are asking 15 bitcoins, or about $297,279, for 80GB of stolen data, which they are selling on both Russian and English-language forums. Cybercriminals even assert that they have already sold data to at least one customer.
According to the report, NATO is looking into one of the company’s suppliers as a potential source of the breach. AirBus, BAE Systems, and Leonardo are the three major shareholders in the joint venture known as MBDA. Although the business is based in Europe, it has affiliates worldwide, including MBDA Missile Systems in the United States.



The organization is coordinating with Italian authorities, where the breach happened.
In addition to NATO, the US military, and the UK Ministry of Defense, MBDA reported $3.5 billion in revenue last year.
Classified Data & Ukraine
According to the BBC, hackers stated in their advertisement for the stolen information that they had “classified information about employees of companies that took part in the development of closed military projects,” along with “design documentation, drawings, presentations, video and photo materials, contract agreements, and correspondence with other companies”
A presentation that appears to provide blueprints for the Land Ceptor Common Anti-Air Modular Missile (CAMM), including the precise location of the electronic storage unit within, is one of the sample files in a 50-megabyte cache that the BBC was able to view.
According to the report, one of these missiles, which is a part of the Sky Sabre system, was recently sent to Poland for use in the conflict in Ukraine.
The fact that advanced persistent threats (APTs) allied with Russia started attacking Ukraine with cyberattacks even before the Russian invasion that took place on February 24 may offer some insight into the motivation of threat actors.
Threat actors continued to suffocate Ukraine with a cyberwar after the physical conflict started in order to support the Russian military’s efforts.
According to the report, documents marked “NATO CONFIDENTIAL,” “NATO RESTRICTED,” and “Unclassified Controlled Information” were also among the sample data the BBC viewed. At least one stolen folder includes thorough blueprints for MBDA hardware.
According to the report, the criminals also emailed the BBC documents, including two that were marked “NATO SECRET.” The content’s origin—whether it came from a single compromised source or multiple sources—was not confirmed by the hackers.
The company’s verification procedures, according to MBDA, “indicate that the data made available online are neither classified data nor sensitive,” despite this insistence.
They have a campus in New Delhi India as well it will be important to monitor what impact it does on the deals in progress and future procurements of the Government of India from the Directly Affected companies or related companies.