Security and Privacy Capability Maturity Model (SP-CMM) by SCF, Secure and Privacy by Design Principles Framework
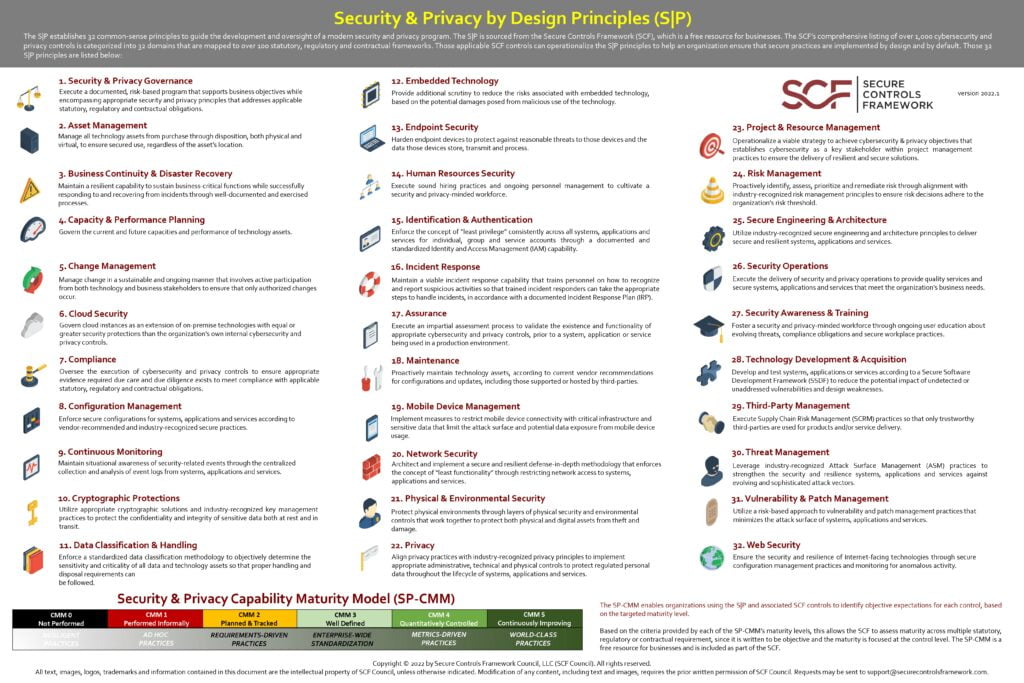
The S|P establishes 32 common-sense principles to guide the development and oversight of a modern security and privacy program. The S|P is sourced from the Secure Controls Framework (SCF), which is a free resource for businesses. The SCF’s comprehensive listing of over 1,000 cybersecurity and
privacy controls is categorized into 32 domains that are mapped to over 100 statutory, regulatory and contractual frameworks. Those applicable SCF controls can operationalize the S|P principles to help an organization ensure that secure practices are implemented by design and by default. Those 32
S|P principles are listed below:
Security & Privacy Capability Maturity Model (SP-CMM)
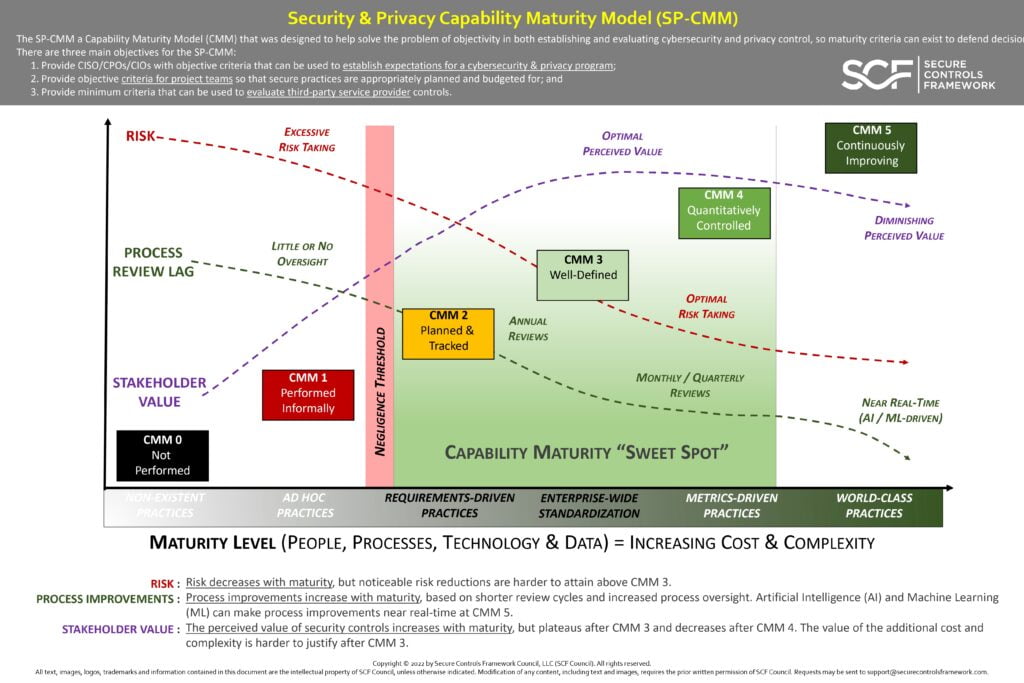
The SP-CMM a Capability Maturity Model (CMM) that was designed to help solve the problem of objectivity in both establishing and evaluating cybersecurity and privacy control, so maturity criteria can exist to defend decision There are three main objectives for the SP-CMM:
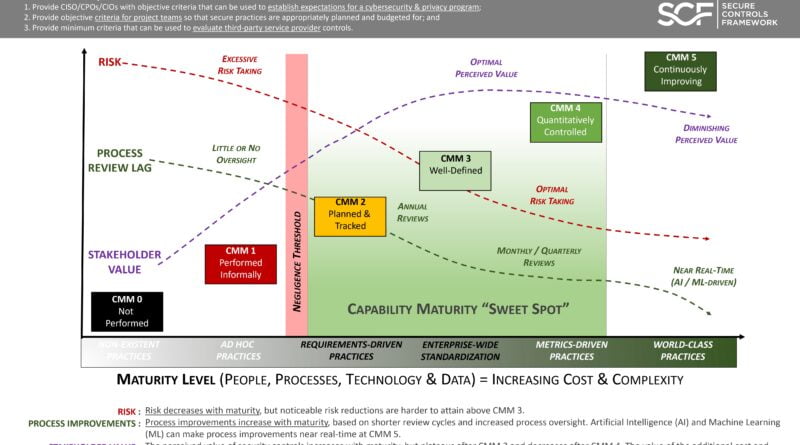
1. Provide CISO/CPOs/CIOs with objective criteria that can be used to establish expectations for a cybersecurity & privacy program;
2. Provide objective criteria for project teams so that secure practices are appropriately planned and budgeted for; and
3. Provide minimum criteria that can be used to evaluate third-party service provider controls.
- Security & Privacy Governance
Execute a documented, risk-based program that supports business objectives while encompassing appropriate security and privacy principles that address applicable statutory, regulatory, and contractual obligations.
- Asset Management
Manage all technology assets from purchase through disposition, both physical and virtual, to ensure secured use, regardless of the asset’s location.
- Business Continuity & Disaster Recovery
Maintain a resilient capability to sustain business-critical functions while successfully responding to and recovering from incidents through well-documented and exercised processes.
- Capacity & Performance Planning
Govern the current and future capacities and performance of technology assets.
- Change Management
Manage change in a sustainable and ongoing manner that involves active participation from both technology and business stakeholders to ensure that only authorized changes occur.
- Cloud Security
Govern cloud instances as an extension of on-premise technologies with equal or greater security protections than the organization’s own internal cybersecurity and privacy controls.
- Compliance
Oversee the execution of cybersecurity and privacy controls to ensure appropriate evidence required due care and due diligence exists to meet compliance with applicable statutory, regulatory and contractual obligations.
- Configuration Management
Enforce secure configurations for systems, applications and services according to vendor-recommended and industry-recognized secure practices.
- Continuous Monitoring
Maintain situational awareness of security-related events through the centralized collection and analysis of event logs from systems, applications and services.
- Cryptographic Protections
Utilize appropriate cryptographic solutions and industry-recognized key management practices to protect the confidentiality and integrity of sensitive data both at rest and in transit.
- Data Classification & Handling
Enforce a standardized data classification methodology to objectively determine the sensitivity and criticality of all data and technology assets so that proper handling and disposal requirements can be followed.
- Embedded Technology
Provide additional scrutiny to reduce the risks associated with embedded technology, based on the potential damages posed from malicious use of the technology.
- Endpoint Security
Harden endpoint devices to protect against reasonable threats to those devices and the data those devices store, transmit and process.
- Human Resources Security
Execute sound hiring practices and ongoing personnel management to cultivate a security and privacy-minded workforce.
- Identification & Authentication
Enforce the concept of “least privilege” consistently across all systems, applications and services for individual, group and service accounts through a documented and standardized Identity and Access Management (IAM) capability.
- Incident Response
Maintain a viable incident response capability that trains personnel on how to recognize and report suspicious activities so that trained incident responders can take the appropriate steps to handle incidents, in accordance with a documented Incident Response Plan (IRP).
- Assurance
Execute an impartial assessment process to validate the existence and functionality of appropriate cybersecurity and privacy controls, prior to a system, application or service being used in a production environment.
- Maintenance
Proactively maintain technology assets, according to current vendor recommendations for configurations and updates, including those supported or hosted by third-parties.
- Mobile Device Management
Implement measures to restrict mobile device connectivity with critical infrastructure and sensitive data that limit the attack surface and potential data exposure from mobile device usage.
- Network Security
Architect and implement a secure and resilient defense-in-depth methodology that enforces the concept of “least functionality” through restricting network access to systems, applications and services.
- Physical & Environmental Security
Protect physical environments through layers of physical security and environmental controls that work together to protect both physical and digital assets from theft and damage.
- Privacy
Align privacy practices with industry-recognized privacy principles to implement appropriate administrative, technical and physical controls to protect regulated personal data throughout the lifecycle of systems, applications and services.
- Project & Resource Management
Operationalize a viable strategy to achieve cybersecurity & privacy objectives that establishes cybersecurity as a key stakeholder within project management practices to ensure the delivery of resilient and secure solutions.
- Risk Management
Proactively identify, assess, prioritize and remediate risk through alignment with industry-recognized risk management principles to ensure risk decisions adhere to the organization’s risk threshold.
- Secure Engineering & Architecture
Utilize industry-recognized secure engineering and architecture principles to deliver secure and resilient systems, applications and services.
- Security Operations
Execute the delivery of security and privacy operations to provide quality services and secure systems, applications and services that meet the organization’s business needs.
- Security Awareness & Training
Foster a security and privacy-minded workforce through ongoing user education about evolving threats, compliance obligations and secure workplace practices. Technology Development & Acquisition
- Technology Development & Acquisition
Develop and test systems, applications or services according to a Secure Software Development Framework (SSDF) to reduce the potential impact of undetected or unaddressed vulnerabilities and design weaknesses.
- Third-Party Management
Execute Supply Chain Risk Management (SCRM) practices so that only trustworthy third-parties are used for products and/or service delivery.
- Threat Management
Leverage industry-recognized Attack Surface Management (ASM) practices to strengthen the security and resilience systems, applications and services against evolving and sophisticated attack vectors.
- Vulnerability & Patch Management
Utilize a risk-based approach to vulnerability and patch management practices that minimizes the attack surface of systems, applications and services.
- Web Security
Ensure the security and resilience of Internet-facing technologies through secure configuration management practices and monitoring for anomalous activity
RISK : Risk decreases with maturity, but noticeable risk reductions are harder to attain above CMM 3.
PROCESS IMPROVEMENTS : Process improvements increase with maturity, based on shorter review cycles and increased process oversight. Artificial Intelligence (AI) and Machine Learning (ML) can make process improvements near real-time at CMM 5.
STAKEHOLDER VALUE : The perceived value of security controls increases with maturity, but plateaus after CMM 3 and decreases after CMM 4. The value of the additional cost and complexity is harder to justify after CMM 3.
-1-390x205.png)
-390x205.png)