Why Threat Modeling Is Important and What It Is
Identifying and evaluating threats that an attacker (threat) could exploit is done through the exercise of threat modelling. Consider a threat model for your home to help you better understand threat modelling. Your home likely has assets, or things that an attacker would value, like cash, jewellery, televisions, and computers. You probably also want to keep your family safe. Perhaps you have a garage where you keep your cars, bikes, and other valuable possessions.
Thinking about potential negative outcomes for your home is the first step in conducting a threat model.For instance, a thief could break in and steal your possessions, or your kitchen could catch fire from cooking grease. You decide what you can do to mitigate the threats after you’ve identified any potential weak points a threat could exploit. The threat model would include locks for the easily accessible doors and windows in the case of a break-in. You might rate the risk as being higher and install an alarm system, bars on ground floor windows, motion-activated lighting, or cameras if your neighbourhood has recently seen a number of break-ins. Sprinkler systems or smoke alarms might be mandated by insurance standards. Include education and training (don’t open the door for the pizza delivery guy when you haven’t ordered pizza) if you think social engineering attacks are a threat.
In other words, the threat model predicts the worst-case scenarios that could happen to the house and recommends controls to lower the risk associated with those threats.
Modeling Threats in Software
The same methodology is used by the engineering, security, and compliance teams when threat modelling new applications and systems. They locate entry points for vulnerabilities into the application and specify controls to lessen the risk those vulnerabilities pose. They search for common weaknesses in the application’s technology stack, including the programming language, frameworks, and deployment environment, rather than focusing on doors and windows. They also cover the application’s regulatory requirements.
The controls necessary to mitigate each specific threat are then defined. The use of particular encryption algorithms, the least-privilege principle, forcing timeouts after failed authentication, and other security controls are some examples of these. Validating all untrusted input is another.
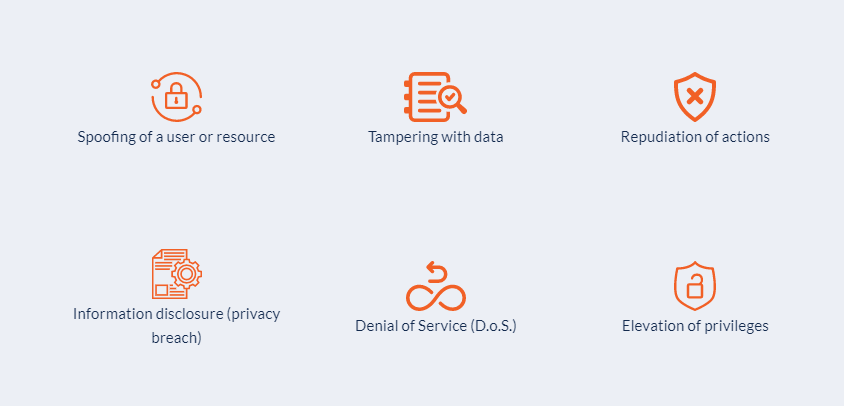
Microsoft invented threat modelling in the late 1990s to develop a “proactive security analysis process.” Microsoft called their strategy STRIDE, which stands for the six types of threats that applications encounter:
Security Compass
With direct integration into current DevSecOps tools and workflows, Security Compass, a pioneer in application security, enables businesses to move to the left and design secure applications from the ground up. By adopting an automated, developer-centric strategy for threat modelling, secure development, and compliance, its flagship product, SD Elements, assists organisations in reducing cyber risks and speeding up the time it takes to market software. Leading financial and technology companies, the U.S. Department of Defense, governmental organisations, and well-known international brands operating in numerous industries rely on Security Compass as their trusted solution provider.