Organizations in Poland and Ukraine are affected by the new “Prestige” ransomware.
The Microsoft Threat Intelligence Center (MSTIC) has found evidence of a novel ransomware campaign using a hitherto unidentified ransomware payload that targets businesses in the logistics and transportation sectors in Poland and Ukraine. On October 11, we saw the introduction of this new ransomware, which refers to itself in its ransom note as “Prestige ransomware,” in attacks that took place across all victims within an hour of one another.
This ransomware campaign stood out from others that Microsoft tracked thanks to a number of distinguishing characteristics:
The spread of ransomware across entire organizations is uncommon in Ukraine, and this activity was unrelated to any of the 94 ransomware activity groups that Microsoft is currently monitoring.
Microsoft was unaware of the Prestige ransomware prior to this deployment.
The activity overlaps with prior FoxBlade victims and shares victimology with recent Russian state-aligned activity, particularly in affected regions and nations (also known as HermeticWiper)
The campaign is distinct from recent destructive attacks utilizing AprilAxe (ArguePatch)/CaddyWiper or Foxblade (HermeticWiper), which have impacted numerous critical infrastructure organizations in Ukraine over the past two weeks, despite using similar deployment techniques. MSTIC is still conducting investigations but has not yet connected this ransomware campaign to a recognized threat group. This activity is being monitored by MSTIC as DEV-0960.
Microsoft uses the DEV-#### designations as a temporary name for a cluster of threat activity that is unknown, emerging, or developing. This enables MSTIC to track the activity as a distinct set of information until we have high confidence in the origin or identity of the actor responsible for the activity. A DEV is changed into a named actor or combined with other actors once it satisfies the requirements.
This blog aims to inform readers and the larger security community about indicators of compromise (IOCs) and other security-related information. Microsoft is still keeping an eye on this and is currently notifying customers who have been affected by DEV-0960 but have not yet been ransomed.Additionally, MSTIC is actively collaborating with other strategic partners and members of the broader security community to share knowledge that can be used to counter this constantly changing threat.
The activity of actors as seen
Ransomware prevention measures
The DEV-0960 activity utilized the following two remote execution utilities before releasing ransomware:
A commercially available tool for agentless remote code execution is called RemoteExec.
An open-source script-based solution for remote code execution is Impacket WMIexec.
In some of the environments, DEV-0960 used these tools for privilege escalation and credential extraction to gain access to highly privileged credentials:
WinPEAS is a set of scripts that can be used to escalate privileges on Windows.
Comsvcs.dll is used to steal credentials by dumping the memory of the LSASS process.
Active Directory database backups are made using ntdsutil.exe, probably for future use.
deployment of ransomware
In all instances where a ransomware deployment was seen, the attacker already had access to extremely privileged credentials, such as Domain Admin. Although the initial access point has not yet been found, in some cases it’s possible that the attacker already had access to the highly privileged credentials as a result of a previous compromise. In these situations, the attacker already has Domain Admin access and is prepping their ransomware payload at the beginning of the attack timeline.
Unless a security configuration forbids it, most ransomware operators develop a preferred set of tradecraft for the deployment and execution of their payload, and this tradecraft typically remains consistent across victims.
The methods used to spread the ransomware for this DEV-0960 activity varied between the environments of the victims, but it does not appear that this was because different security configurations prevented the attacker from using the same methods in each environment. This is particularly noteworthy because each ransomware deployment took place within an hour. The different strategies for ransomware distribution were:
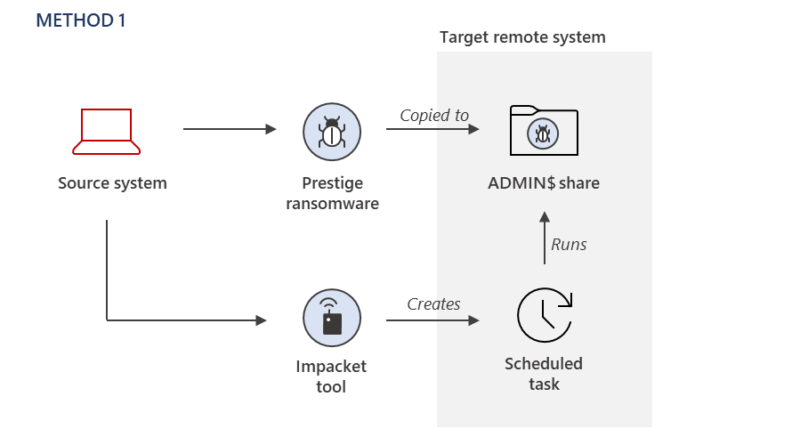
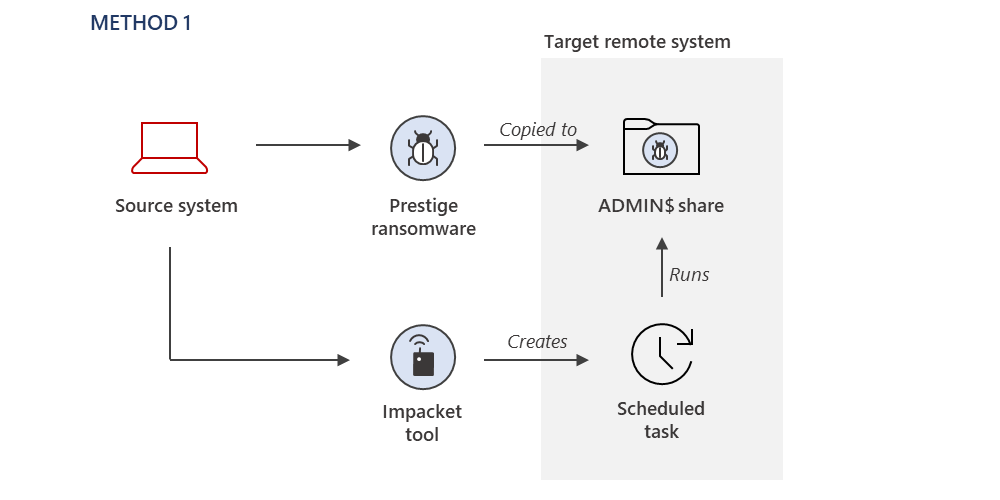
Method 1: Impacket is used to remotely create a Windows Scheduled Task on target systems in order to execute the ransomware payload after the ransomware payload has been copied to the ADMIN$ share of a remote system.
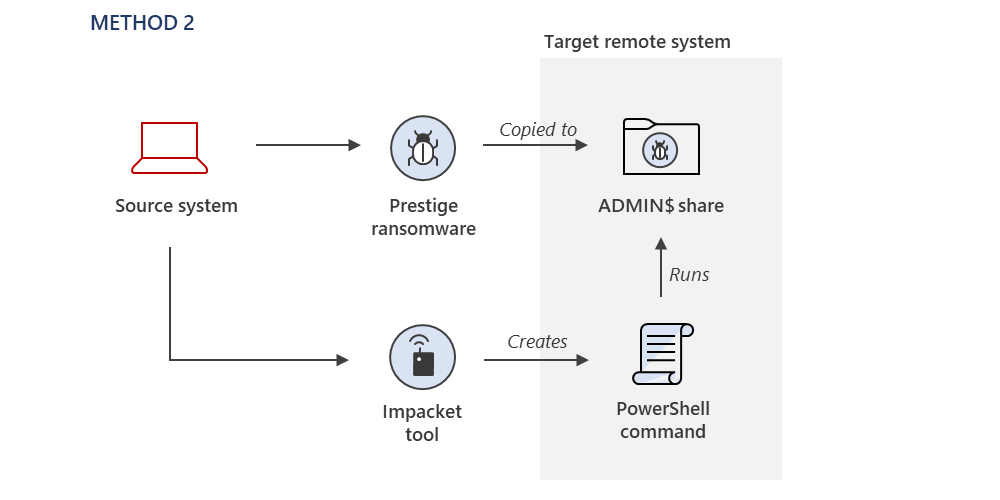
Method 2: The ransomware payload is copied to a remote system’s ADMIN$ share, and Impacket is used to remotely execute a PowerShell command that has been encoded on the target systems.
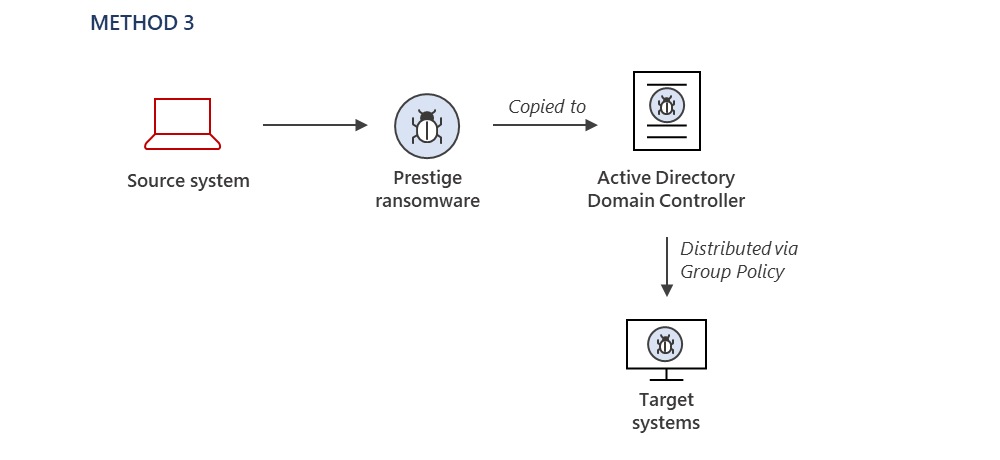
Method 3: Using a Default Domain Group Policy Object, the ransomware payload is copied to an Active Directory Domain Controller and distributed to systems.
Recommendations for customers
After an initial compromise involving gaining access to highly privileged credentials, the actor released the ransomware payload. By following the security recommendations given below, the methods used by the actor and described in the “Observed Actor Activity” section may be lessened:
To prevent lateral movement using the WMIexec component of Impacket, block process creations originating from PSExec and WMI commands.
To stop attacks from stopping or interfering with Microsoft Defender, enable Tamper protection.
To cover rapidly changing attacker tools and techniques, enable cloud-delivered protection in Microsoft Defender Antivirus or its equivalent. The vast majority of novel and untested variants are blocked by cloud-based machine learning security measures.
Despite the fact that this attack is different from conventional ransomware, avoiding the credential theft, lateral movement, and ransomware deployment techniques used by DEV-0960 is possible by following our advice on defending against ransomware.
Investigate whether they exist in your environment and make an assessment of any potential intrusions using the indicators of compromise that are included.
To reduce the risk of credentials being stolen, enable multifactor authentication (MFA) and make sure that it is enforced for all remote connectivity, including VPNs. All customers are urged to download and use password-less programs like Microsoft Authenticator to protect their accounts by Microsoft.
indications of a compromise (IOCs)
The IOCs seen during our investigation are listed in the following table. We advise our customers to look into these indicators in their environments and put detections and safeguards in place in order to spot previous related activity and stop future attacks on their systems.
| Indicator | Type | Description |
| 5dd1ca0d471dee41eb3ea0b6ea117810f228354fc3b7b47400a812573d40d91d | SHA-256 | Prestige ransomware payload |
| 5fc44c7342b84f50f24758e39c8848b2f0991e8817ef5465844f5f2ff6085a57 | SHA-256 | Prestige ransomware payload |
| 6cff0bbd62efe99f381e5cc0c4182b0fb7a9a34e4be9ce68ee6b0d0ea3eee39c | SHA-256 | Prestige ransomware payload |
| a32bbc5df4195de63ea06feb46cd6b55 | Import hash | Unique PE Import Hash shared by ransomware payloads |
| C:\Users\Public\README | File path | File path of the ransom note |
Detections
Microsoft 365 Defender
Microsoft Defender Antivirus
Microsoft Defender Antivirus detects known Prestige ransomware payloads with the following detection:
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint provides alerts for the indicators used by DEV-0960 discussed above.
- Ransomware-linked emerging threat activity group DEV-0960 detected
Microsoft Defender for Endpoint also provides alerts for the pre-ransom techniques discussed above.
Customers should act on these alerts as they indicate hands-on-keyboard attacks. NOTE: These alerts are not uniquely tied to the Prestige ransomware nor to the campaign discussed.
- Ongoing hands-on-keyboard attack via Impacket toolkit
- WinPEAS tool detected
- Sensitive credential memory read
- Password hashes dumped from LSASS memory
- Suspicious scheduled task activity
- System recovery setting tampering
- File backups were deleted
Advanced hunting queries
Microsoft Sentinel
Prestige ransomware file hashes
This query looks for file hashes and Microsoft Defender Antivirus detections associated with Prestige ransomware payload.
Microsoft 365 Defender
Impacket WMIexec usage
This query surfaces Impacket WMIexec usage on a device:
DeviceProcessEvents
| where Timestamp >= ago(7d)
| where FileName =~ "cmd.exe"
| where ProcessCommandLine has_all (@" 1> \127.0.0.1\", "/Q ", "/c ", @" 2>&1")
| where InitiatingProcessFileName =~ "WmiPrvSE.exe"
This query has the same purpose as above, but it also groups all the commands launched using Impacket WMIexec on the device:
DeviceProcessEvents | where Timestamp >= ago(7d) | where FileName =~ "cmd.exe" | where ProcessCommandLine has_all (@" 1> \127.0.0.1\", "/Q ", "/c ", @" 2>&1") | where InitiatingProcessFileName =~ "WmiPrvSE.exe" | project DeviceName, DeviceId, Timestamp, ProcessCommandLine | summarize make_set(ProcessCommandLine), min(Timestamp), max(Timestamp) by DeviceId, DeviceName
LSASS process memory dumping
This query surfaces attempts to dump the LSASS process memory comsvcs.dll:
let startTime = ago(7d);
let endTime = now();
DeviceProcessEvents
| where Timestamp between (startTime..endTime)
| where FileName =~ 'rundll32.exe'
and ProcessCommandLine has 'comsvcs.dll'
and ProcessCommandLine has_any ('full','MiniDump')
| where not (ProcessCommandLine matches regex @'{[\w\d]{8}-[\w\d]{4}-[\w\d]{4}-[\w\d]{4}-[\w\d]{12}}'
and ProcessCommandLine matches regex @'(\d{2}_){3}' )