Canarytokens. org – Rapid, Free, Mass Detection
Introduction
Web bugs, the transparent images that monitor email opening, are probably already familiar to you. They operate by inserting a special URL in the image tag of a page and keeping an eye on incoming GET requests.
Imagine doing that instead for file reads, database searches, process executions, log file patterns, Bitcoin transactions, or even Linkedin profile views. All of this is accomplished by Canarytokens, which enables you to implant traps in your production systems rather than erecting separate honeypots.
You can download and use your own installation of Canarytokens for free at http://canarytokens.org (source and Docker images are available.)

Why ought you to care?
Network intrusions do occur. from governments to large corporations. from unaware grandmothers to renowned security experts. This is kind of understandable. Finding out about it months or years later is not acceptable.
A free, quick, and painless way for defenders to learn that they have been breached is with canary tokens (by having attackers announce themselves.)
Token operation (in 3 easy steps):
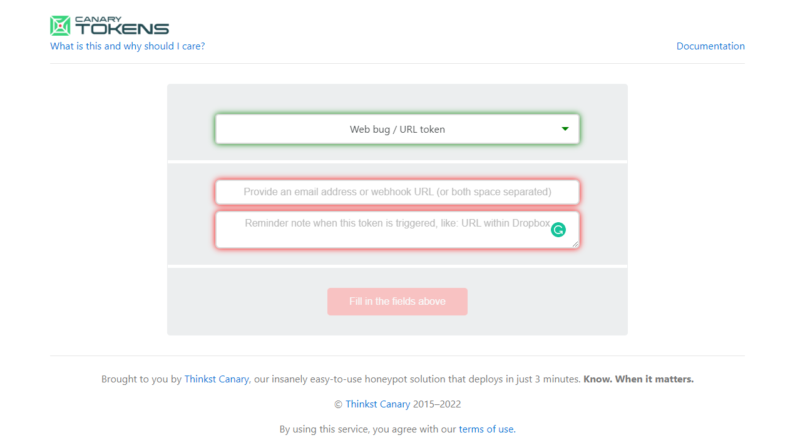
Visit the website to obtain a gratis token (which could look like an URL or a hostname, depending on your selection.)
We will send you an out-of-band (email or SMS) notification if the token is ever used by an attacker to visit a website.
As an added bonus, we provide you with numerous tips and tools that raise the probability that an attacker will trip over a canary token.
More information
A distinctive identifier makes up tokens (which can be embedded in either HTTP URLs or in hostnames.) We email the address associated with the token with a notification each time that URL is accessed or the hostname is found. All you need is your browser to get one in a matter of seconds.
How to get a token
Pay a visit to canarytokens.org.
your email address. (Mails are not used for any other purpose; they are only used to notify you when the token is triggered.)
Write a comment outlining how and where you’ll be using the token. A comment on the token will help you remember where you put it if it is activated in six months.
Use phrases like “file watch on 192.168.100.2:/repos/repo3/README.txt” or “Password lure email in user@domain.com inbox” to be more precise. We anticipate using a lot of tokens, so a thorough description is required.
To get your token, click “Generate Token.”
Copies of the token should be placed in high-traffic areas.
How do thieves knock a token over?
Remember that a typical token is an exclusive hostname or URL. The URL element has a lot of flexibility. As a result, if your token is:
http://canarytokens.com/terms/5vicnyy8rjrud11p8t83o6tv6/contact.php
subsequently, a visitor to any of these:
http://canarytokens.com/terms/5vicnyy8rjrud11p8t83o6tv6/admin.asp
http://canarytokens.com/terms/5vicnyy8rjrud11p8t83o6tv6/admin.asp
http://canarytokens.com/includes/5vicnyy8rjrud11p8t83o6tv6/login.docx
http://canarytokens.com/foo/bar/5vicnyy8rjrud11p8t83o6tv6/anything-really would still make your token active. This provides us with the most basic use-case for a token, a traditional web-bug.
You could, for instance, send yourself an email containing the following text along with a link to the token:

You know not to touch it, so just leave it in your inbox unread. An intruder who has taken control of your mail spool does not. Your week is about to get worse, but at least you know if your emails are stolen, an attacker who is reading them should be drawn to the mail and visit the link.
You could even use the same token as an embedded image if you’d like. This mimics the functionality of the standard 1×1 transparent GIF. Now that his mail client renders remote images, an attacker browsing your inbox could accidentally stumble upon it. Free Canarytokens can be used in this manner as a traditional web/mail-bug to get notified when an email you send has been read.
Canarytokens for use in production
Canarytokens are extremely flexible, as we’ll see, and can be used as straightforward web bugs.
Even if you have a sophisticated SIEM that alerts you to events, you’ll discover that with a little imagination, there are many places where a token—which can be deployed in seconds—can help you win that you wouldn’t otherwise be able to.
Do you believe DropBox’s administrators and support staff to respect your privacy? Office 365? maybe HipChat?)
Create a token, then drop it into your folder or mention it in your HipChat channel. If an administrator stumbles upon your URL while perusing content in their free time (or while being forced to do so by a third party), you will be notified.
Tools plus tokens
FileWatchers
Every time someone is taken advantage of and their home address is made public, there is some speculation as to “how they got taken.” There is something we do know, even though we might not always be able to answer that question. Their home directory’s files were read. (Since this will include files that were never intended to be read by anyone, it could be a very good indicator that something bad has happened!)
We provide a Linux-compliant no-dependency C programme (Canaryfy) that is included. To watch a file, create a token and use it. You will be notified if the watched file is ever read.

Without iNotify events, we use DTrace on OSX to achieve the same outcome.
XXX will accept a token as input and will let you know if someone runs uname, id, ifconfig, or hostname on your machine. You could also use DTrace to monitor binaries as they run.
share.desktop.ini and zip-files
In the form of the venerable old desktop.ini configuration file, Windows offers an even cooler method of notification. Explorer can set a unique icon for a file by dropping a desktop.ini file in a folder. Using DNS, we can effectively use a token as our iconfile because this icon can exist on a distant server (via a UNC path).

This indicates that a notification is sent each time someone uses Explorer to browse the directory! Without any agents or log file monitoring, it is a true file tripwire.
(Both WinZIP and WinRAR respect desktops and preserve directory structures.
Using the desktop, you can download a Zip file.
After you generate your token, ini is already packaged, and you’ll be notified if the Zip file is opened or expanded.
SQL and MySQL
When reading about database security, it’s not uncommon to come across advice like inserting “Canary” rows into a database and then keeping an eye out to see if they are ever accessed. We bet that the majority of those who have offered this advice have never actually attempted to put it into practise. It’s surprisingly difficult and probably impossible with the database version you’re using!
Although it is not natively possible for MSSQL server to perform an action in response to a SELECT statement, it is possible to create a custom VIEW that performs a DNS query in response to a SELECT against the VIEW.

(It is also possible to set the VIEW’s permissions so that anyone can perform a select on it without knowing where the data came from.)
Then, if someone queries the user_password view, for example:

The DNS lookup is triggered an a notification is sent:

Because the DNS query is constructed in T-SQL, we have precise control over it. It implies that we can include more details, such as the user who made the inquiry, in the notification.
We use a different straightforward tool called canarytokend on MySQL. This straightforward tool matches preset regexes, tails the MySQL log file, and generates alerts via the canarytokens console.

Due to its high extensibility, Canarytokend is beneficial because it only tails log files and initiates tokens (MySQL is just the example log file). It can be used to watch any type of log and to light matches for emails.
The Honeydoc file format is comparatively well-known. Just adding a token to the document’s meta-data will reliably ping us when it is opened. Both a Word document and a PDF document are produced by Canarytokens.
One trick: regardless of whether the user permits network communications, the PDF document will cause an alert to be sent by Adobe Reader!
Copy of JS Page
The Canarytoken server can also alert you if a website that matters to you has been copied (and hosted on another site). Typically, step 0 of a successful phishing campaign is this. We simply create our token from canarytokens.org to accomplish this, and then:

Bitcoin, LinkedIn, and Imgur
We have additional channels for the Canarytokens server thanks to Imgur, LinkedIn, and Bitcoin. These websites can be used as oracles to reveal whether they have been accessed or otherwise tampered with.
This is nothing new.
Yes, the fundamental idea is dated. In 2003, Lance Spitzner discussed honeytokens, and Spafford & Kim first brought up the idea in 1994.
In order to catch map thieves, map makers have actually been faking data for hundreds of years.
Canarytokens, on the other hand, simplifies this idea so that it can be used by anyone and employs a number of methods that haven’t been openly discussed.
What if the domain canarytokens.org is blacklisted by hackers? Doesn’t that function?
This is viable! We advise you to run your own server by downloading the canarytokens docker image. (From here, you can download the source to build it yourself.)