Micro Emulation Plans by MITRE-Engenuity
We enjoy imitating the opposition.
In fact, it’s so important that they’ve written, spoken, trained on it, and are still developing and disseminating more emulation plans (including one of the first public Adversary Emulation Plans).
However, many organisations are unable to overcome the entry barrier due to the expense and complexity involved in developing or even carrying out the majority of adversary emulation plans.
The Center for Threat-Informed Defense (Center) collaborated with AttackIQ, Inc., Booz Allen Hamilton, Inc., Citigroup Technology, Inc., Ernst & Young U.S. LLP, Fujitsu, HCA — Information Technology & Services, Inc., IBM Corporation, Microsoft Corporation, and Verizon Business Services to create Micro Emulation Plans in an effort to make adversary emulation accessible to a wider audience.
By using simple to use executable binaries that any user can use, these emulation plans re-imagine adversary emulation to focus on very specific threat-informed defensive objectives.
Currently Used Adversary Emulation
The four general steps that make up an operation when it comes to adversary emulation today are cyber threat intelligence (CTI) research, technique selection, offensive development, and emulation execution.
- An adversary that poses a significant or developing threat is first found through CTI research. To understand the scope, sophistication, and impact of each potential emulation plan, a deeper investigation into each adversary is conducted after a short list of candidates has been created.
- Following the choice of an adversary, they move on to the technique selection phase, where ATT&CK techniques from a variety of tactics are taken from the CTI reporting and put together in an emulation scenario.
- Offensive development can start once ATT&CK techniques have been incorporated into a scenario. Tools and commands are created in this phase to replicate the chosen scenario.
- Emulation execution can then start, usually under the supervision of an experienced red team operator.
This workflow makes it easier to create and deliver threat-informed assessments that let defenders practise breaches and learn from real-world threat activity. The four-step process from research to execution, though, can take a lot of time and coordination between many different, specialised skill sets.
Plans for micro-emulations: Concentrating on the Positive
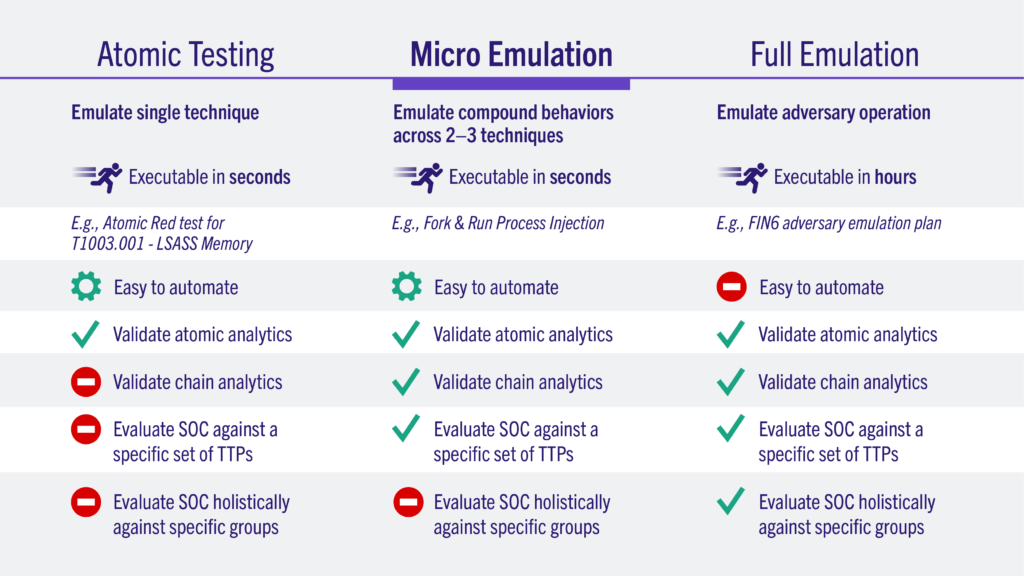
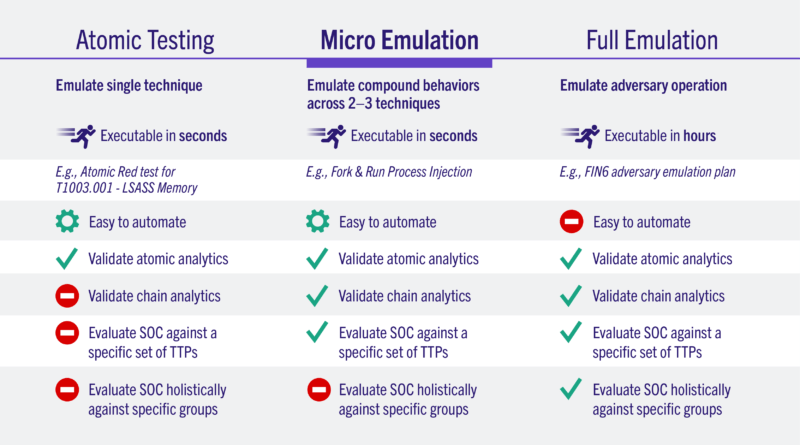
The same four steps are followed by micro emulation plans, but more effectively, as a tailored application of adversary emulation. CTI research is done to find particular compound behaviours that are frequently used across multiple adversaries or campaigns, as opposed to identifying a single adversary and listing all of their various techniques to emulate. Compound behaviours are a collection of tactics used by the same enemy activity. For instance, a lot of payloads will enter a sacrificial process, carry out an action, like executing a command, kill the sacrificial process, and then repeat. In a broader sense, comprehending and simulating the macro intelligence leads us to micro emulation. Many adversaries engage in this “fork & run” behaviour.
In the same way as before, technique selection is carried out, but it is limited to those compound behaviours that are of interest. Additionally, the lifecycle of offensive development is more concentrated. Plans for micro emulation, which concentrate on a much smaller set of techniques, can be created in brief sprints.
Last but not least, execution happens quickly. Simply double-clicking an executable will do it. A micro plan can be carried out by anyone, and you don’t need a complicated environment to do it. Any defender or organisation can now access enemy emulation.
What is inside the box?
Nine micro emulation plans in five different areas of particular interest to defenders are included in our initial release. One plan was created for Linux, and eight plans were created for Windows.
- Data Sources: They wanted to give defenders a chance to establish a baseline for the kinds of information they are gathering. These plans concentrate on three ATT&CK-defined data sources that they believe are frequently underrepresented: named pipes, registry modification, and file access/modification. Before moving on to more adversary-focused emulations, a defender should be able to test and fine-tune how they are logging this important data using one of these plans.
- Web shells: A variety of adversaries use backdoor web servers to gain enduring access to victims. These plans write a web shell to disc, connect to the shell over the network, and then run several discovery commands. They created a strategy for both Windows and Linux in this area.
- Fork & Run: As was already mentioned, the fork-and-run strategy creates sacrifice processes that are later injected to carry out a number of discovery commands. This is comparable to the payload of a typical beacon.
- Post-Phishing User Execution: These plans carry out actions that are likely to take place after a user has received a malicious payload. The traditional malicious Office macro, the slightly less traditional but still prevalent.lnk file, and the rapidly gaining more and more popularity.iso container were used as the basis for our three different emulations.
- Active Directory Enumeration: This plan produces the telemetry linked to a few typical active directory discovery behaviours you might observe prior to privilege escalation and/or lateral movement. Any environment in which this plan is executed will allow it to run, but only a domain will allow it to do so with complete results.
What are their uses?
In order to accommodate defenders who might not have access to an advanced red team, they created micro emulation plans. These strategies can be carried out manually from a command-line, quickly and easily with a double-click, or by using already available red team tools. You can find instructions for integrating micro emulation plans into another tool (using CALDERA as an example) on our GitHub page, but our plans ought to work with any breach and attack simulation tool. A defender can produce and start learning from the emulation telemetry shortly after execution. Each plan includes supporting documentation for:
- Describe the mimicked behaviours: Who or what are they?
- Background: Why should you be concerned?
- Execution Guidelines / Resources, including a demonstration and details on how to alter each micro plan: How do I make it run?
- Defensive Lessons Learned, emphasising opportunities for detection and mitigation How can I proceed?
Adversary Emulation’s Future
Are plans for micro emulation the answer to every problem that conventional adversary emulation presents? No, but they are a low-effort, high-impact option to take into account when creating an emulation plan.
They continue to place a high value on complete adversary emulation plans because they can help defenders better understand how a breach feels.
They also appreciate Atomic Red Team’s work because it is quick, simple to use, and frees defenders to concentrate on a variety of unit testing. The gap between the two, in our opinion, is filled by micro emulation plans. Defenders can easily and quickly test their defences against carefully crafted and threat-informed groupings of adversary techniques by using micro emulation plans.
They’ve added micro emulation plans to the Adversary Emulation Library to make sure they’re simple to find. They see this as just the beginning and intend to create more micro emulation strategies in the future.
Available adversary emulation plans are listed below:
Getting Starting with Micro Emulation Plans
Similar to full emulation plans, micro emulation plans are a type of adversary emulation that is designed to help us test and tune our defenses. However, these plans can be executed without a red team and without the need for an offensive assessment. Each plan is still composed of an intelligence overview for the behaviors being emulated, however we are emulating behaviors that are common across multiple adversaries as opposed to a singular adversary.
These plans are easy to execute, with no dependencies needed or special configuration of your environment. All plans can be executed from either a standalone or networked machine. They can be executed manually or integrated into automation software. We have provided an example of how to execute a plan with CALDERA, but these plans can be broadly applied to other platforms.
Each micro plan has default runtime options, however, detailed instructions can be found on the README for each plan on how to customize execution to fit your specific needs. We have included the source code and BUILD instructions for each plan, so that they can be modified and recompiled, as needed.
The micro plans can be downloaded from the Releases page.