To protect networks and data, CISA believes that understanding the behavior of adversaries is crucial. The success of network defenders in detecting and mitigating cyberattacks depends on this understanding. One tool that helps with this is the MITRE ATT&CK® framework, which is a knowledge base of adversary tactics and techniques based on real-world observations. It’s used by network defenders in the private sector, government, and the cybersecurity product and service community to develop specific threat models and methodologies. It’s freely accessible to any person or organization in the hopes of creating more effective cybersecurity solutions.
CISA uses the MITRE ATT&CK framework to identify and analyze adversary behavior. It provides information on more than 100 threat actor groups, including the techniques and software they use. Network defenders can use the framework to identify gaps in defenses, assess the capabilities of security tools, organize detections, hunt for threats, engage in red team activities, or validate mitigation controls. CISA encourages the use of the framework because it provides a common language for analyzing threat actors.
To help network defenders make better use of the MITRE ATT&CK framework, CISA developed the Best Practices for MITRE ATT&CK Mapping guide. This guide provides clear guidance, examples, and step-by-step instructions for analyzing and reporting on cybersecurity threats. Following these best practices will improve defenders’ ability to proactively detect adversary behavior and support robust, contextual sharing of information to strengthen the security of systems, networks, and data. CISA worked with the Homeland Security Systems Engineering and Development Institute™ (HSSEDI) and the MITRE ATT&CK team to develop this guide.
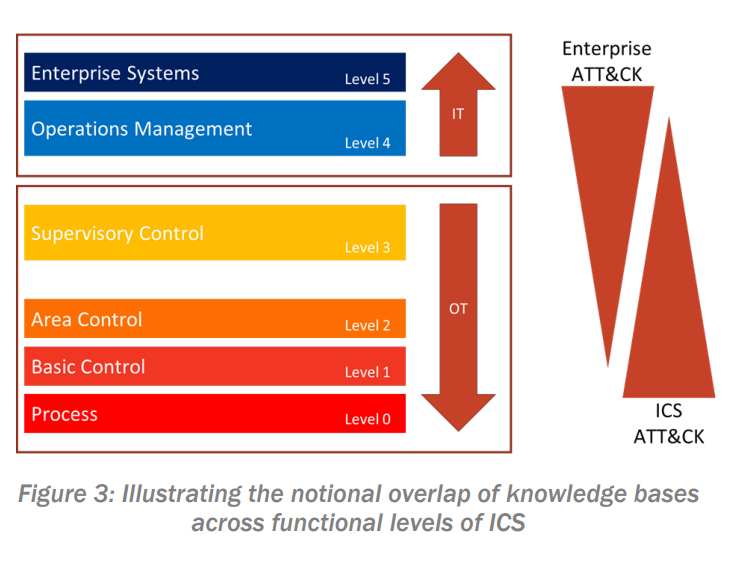
across functional levels of ICS
Note: In January 2023, CISA and HSSEDI updated the best practices guide to cover changes made to the framework since its initial publication in June 2021. The update also includes guidance for mapping industrial control systems (ICS) and addresses common analytical biases and mapping mistakes.