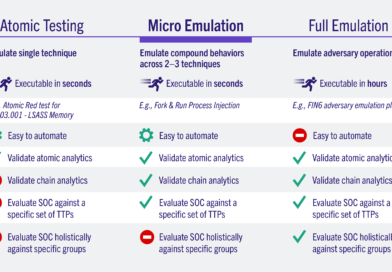
We enjoy imitating the opposition. In fact, it’s so important that they’ve written, spoken, trained on it, and are still developing and disseminating more emulation plans (including one of the first public Adversary Emulation Plans). However, many organisations are unable to overcome the entry barrier due to the expense and complexity involved in developing or even carrying out the majority of adversary emulation plans. The Center for Threat-Informed Defense (Center) collaborated with AttackIQ, Inc., Booz Allen Hamilton, Inc., Citigroup Technology, Inc., Ernst & Young U.S. LLP, Fujitsu, HCA — Information Technology & Services, Inc., IBM Corporation, Microsoft Corporation, and Verizon Business Services to create Micro Emulation Plans in an effort to make adversary emulation accessible to a wider audience. By using simple to use executable binaries that any user can use, these emulation plans re-imagine
Offensive

MITRE ATT&CK® Released Updates in Apr 2022 With Additional Techniques and Structuring
The Techniques, Groups, and Software for Enterprise, Mobile, and ICS are updated in the April 2022 (v11) ATT&CK release. The
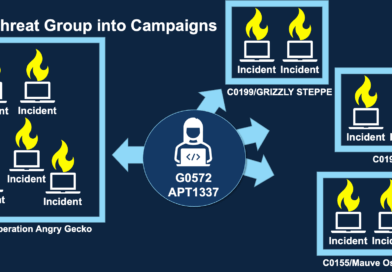
Campaigns to be Introduced to MITRE ATT&CK V12
Primary Articles Published by Matt Malona In ATT&CK 2022 roadmap, at ATT&CKCon 3.0, and most recently on the SANS Threat

Beta Mobile Sub-Techniques, Structured Detections, and ICS Join the Band as ATT&CK Upgrades to Version 11
The most recent ATT&CK release is now available, and this time They have upgraded to version 11! There shouldn’t be

MITRE ATT&CK® Released Updates in Oct 2021 With Additional Techniques and Structuring
MITRE ATT&CK® is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge
- Advertisement ( 300*250 ) -
Latest News
Malware Analysis Report on a malicious listener deployed on Ivanti Endpoint Manager Mobile (EPMM) systems
U.S. Cybersecurity and Infrastructure Security Agency’s new Malware Analysis Report on a malicious listener deployed on Ivanti Endpoint Manager Mobile