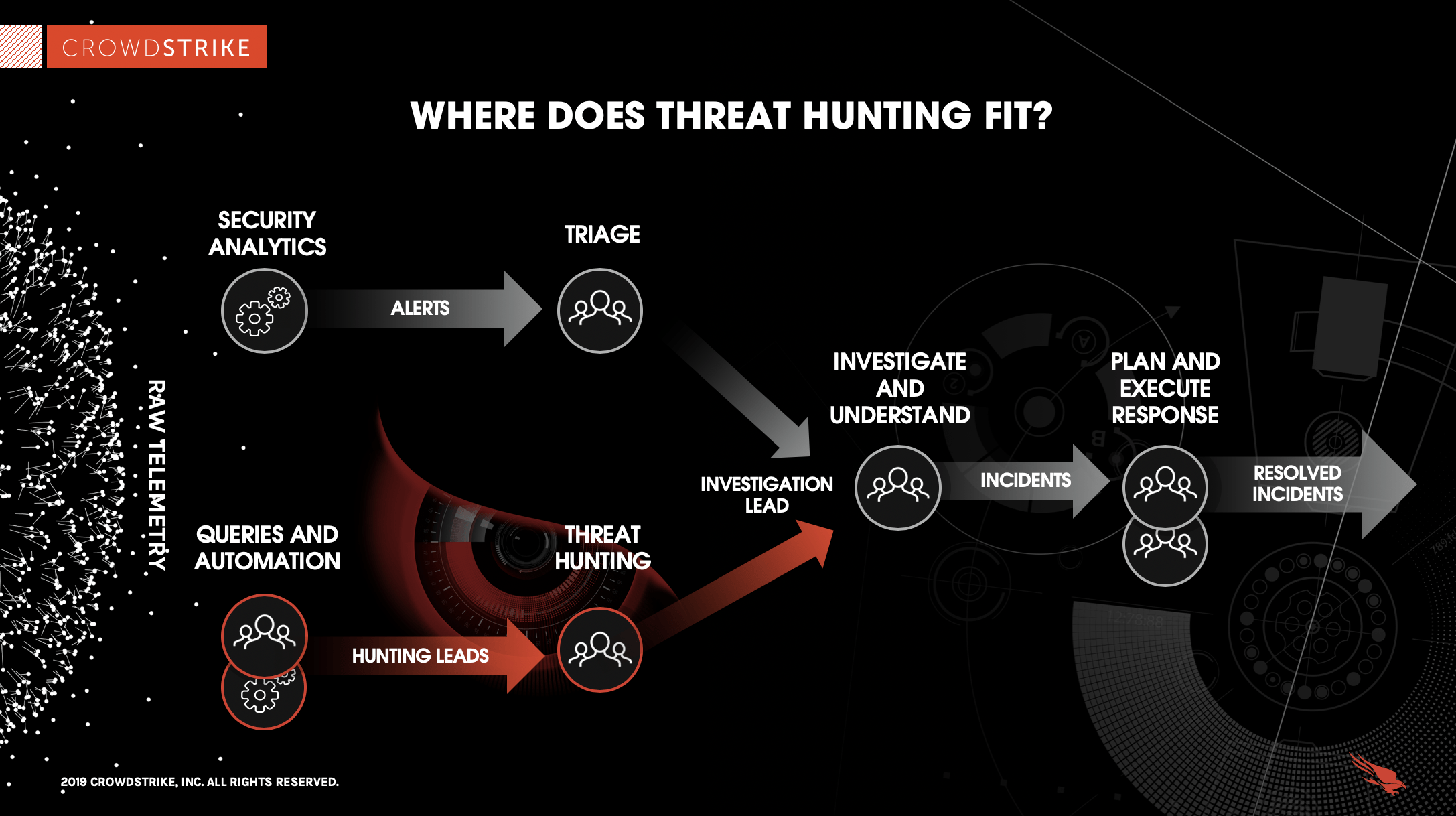
“Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses.” ~ Crowdstrike
An increase in high-profile industry security issues over the past few years (PDF) has made offensive tactics one of the top priorities for businesses looking to reduce the risk of an attack. Potential security risks cannot be ignored or left to chance, and an emphasis on developing stronger defensive security tactics, working in tandem with offensive security teams, is crucial for identifying the behaviors of potential threats and creating stronger defenses against evolving challengers. Many businesses have chosen to maintain remote and hybrid working environments.
Particularly, threat hunting has become a crucial element of corporate security. In order to create defenses against threats, it includes the tasks of identifying patterns of threat behaviors and looking for anomalies and changes in an environment based on suspicious activity.
SEARCH-Anchored Threat Hunting
The following six steps must be completed by threat hunters in an iterative “SEARCH” cycle in order to carry out the best threat-hunting procedures.
Sense
Enrich
Analyze
Reconstruct
Communicate
Hone
Sense: You need hunting grounds to look for threats. A solid foundation is built by gathering extensive and deep telemetry data that completely captures behaviors and activity throughout the entire organization’s network. It sets the parameters for the hunt, enabling hunters to concentrate and concentrate their efforts.
Enrich: You must add context and threat intelligence to the telemetry data in order to fully comprehend what it is trying to tell you. Without enrichment, it can be challenging to make sense of raw telemetry data, increasing the likelihood that an attack will go unnoticed.
What constitutes “normal” in our corporate environment, and why? What do we know about the actions of an attacker? Which systems are frequently connected to one another? This context sieve allows for a more focused search for potential non-malware attacks.
Analyze: Threat investigators examine the data to determine whether to confirm any suspicious activity they may have spotted. It requires using intricate statistical techniques, looking at outliers, and performing frequency analysis. Threat hunters develop hypotheses and test them to determine where and how a determined attacker might operate in an effort to go unnoticed. Being able to think like an experienced attacker is a skill that can only be developed through countless hours of sophisticated, laser-focused, and meticulous threat hunting experience. In this stage of the SEARCH process, the human element is crucial because hunters’ expertise can be applied to a variety of threat behaviors and potential intrusions.
Reconstruct: Once the threat hunter has determined that a specific intrusion is important enough to investigate further, it’s time to delve in and sketch a timeline of possible circumstances leading up to the breach. How far has it spread, and has any harm been done so far? Does the manner in which this threat surfaced make sense?
In order for defenders to react to the threat swiftly and effectively, it is important to flesh out a more complete picture.
Communicate: The threat hunter will inform your security operations center (SOC) when an intrusion has been verified and its current scope has been recorded so they can react and thwart attacks successfully.
Hone: The knowledge gained from a successful threat hunt can be applied to technical security controls to help them recognize and stop similar intrusions more quickly and automatically in the future. This enables threat researchers to concentrate their efforts on identifying fresh and inventive cyberattack vectors. Threat hunters and technology coexist, each strengthening the other.
Constantly looking for threats
Ultimately, a smart, creative, and determined defender who is outfitted with the appropriate technology and procedures can stop a smart, creative, and determined intruder in the best way possible.
The SEARCH methodology offers a strong framework for threat hunting, but for it to be truly effective, it must be used continuously. Remember, whether the attack occurs at 1 p.m. or 9 a.m., it only takes 92 minutes for it to spread throughout your body. The most straightforward way to make sure that this methodology works best to protect your data is to make your SEARCH operation continuous.
What, then, makes a threat-hunting program effective? The truth is that it might not be as simple as it seems to spot suspicious activity. To bring the process to life, a comprehensive strategy with proactive manual detection, ongoing team communication, and an investment in the right people are needed.
Finding the Correct Skills
To thoroughly examine suspicious patterns and search the environment for threats that haven’t yet been recognized by a company’s existing security tooling and processes, threat hunting requires a human touch. Finding potential adversaries and advanced persistent threats (APTs), anticipating their next move, and stopping them in their tracks are all highly strategic games of cat and mouse.
A successful threat hunter must have a thorough understanding of their surroundings, be aware of known threats that their team has encountered, and be able to solve problems and think critically about possible covert entry points for adversaries. This serves as the foundation for creating more effective defensive protocols and can be thought of as the pinnacle of detective work. It’s crucial to invest in the right team members and promote an environment that values open communication.
Adobe’s threat-hunting team has developed a messaging bot app that security teams, such as the security operations center or incident response, can use to communicate easily with the hunt team and receive leads or hunt ideas. Hunt reports are distributed to the relevant stakeholders and cross-functional security teams after each successful hunt in order to strengthen the organization’s current security posture.
The hunt team collaborates closely with the detection function to enhance existing techniques and add fresh data based on newly discovered strategies employed by adversaries. Additionally, they work closely with the group in charge of central operational security data to find gaps, and incorrect configurations and enhance data so that security teams can use it more efficiently.
While machine learning and automated processes can undoubtedly help in the hunt, threat hunting still primarily relies on manual procedures. Aggregated data analytics can help reduce the number of time teams must spend searching through data by quickly identifying anomalies in data patterns within a company’s network.
In order to review massive amounts of log data and assist us in identifying anomalies that suggest a user’s or entity’s behavior change, Adobe is developing multiple UEBA (user and entity behavior analytics) pipelines using machine learning and advanced data analytics.
After additional enrichment and correlation, these anomalies are transformed into hunt leads (or alerts) for human review and escalation as necessary.
Putting the brakes on adversaries
With the right team in place, security teams can start outlining their strategy and plan of attack to find APTs:
Support an explanation for how adversaries might possibly access the network.
Set a program goal that is very clear (e.g., reducing time adversaries spend in the network, reducing the number of high-impact threats, etc.)
Examine data for anomalies and collaborate with other teams to create new, more effective defenses.
Malware Lab’s emergence
The malware lab has been around for a while, and although it has gone by many names (“dirty lab” and “threat detection engineering” come to mind), the goal has remained the same: through malware research, improve defenses based on threat actor behaviors and gain better insight into cyber-risk across the entire organization.
The malware lab idea has started to emerge for high-risk enterprises as part of their strategic initiatives aimed at maturing their security programs by filling the cybersecurity talent gap through tool automation and consolidation. As exposures rise, they might also refocus security teams on gaining insight into their adversaries before an attack and on offering assistance to wider digital lines of business. In order to prioritize a malware lab as part of their ongoing digital transformation and pursue a more threat-focused information security approach, CISOs have specifically mentioned the following factors.
– Recognizing Their Opponents
Not only the adversaries but also the attack tactics they use and the associated IOCs (indicators of compromise). With the help of this crucial threat intelligence, organizations can take proactive measures and decide what to do in response to potential threats based on current trends.
-Building an Excellence Center
a location to manage file analysis and related best practices that would give visibility into any malware that has already infiltrated or might do so.
-Improving Their Capabilities for Detection and Response
This goes beyond deploying controls more effectively and efficiently and curating external threat feeds.
-Developing Predictive Security Strategies
adopting a proactive mindset to anticipate events and understand potential adversary capabilities, attack strategies, and targets.
How Do Malware Labs Work?
The malware lab provides access to knowledge and threat management resources while centralizing file investigation services. Enterprises can quickly create and advance a more sophisticated and cyber-resilient digital environment through a more automated unified threat analysis platform and detection infrastructure.
Among the crucial elements of a malware lab are:
UTAEC, or Unified Threat Analysis Engine and Console
The malware lab is powered by the core analysis engine, which also unifies threat analysis capabilities such as automated static and dynamic analysis (i.e., sandboxing technologies). Instead of slogging through manual tools and disjointed data, threat analysts, researchers, and hunters collaborate on a single console or workbench to operationalize the resulting intelligence and implement risk mitigation strategies.
Comprehensive Threat Intelligence Repository The source of truth that offers a reliable archive of local and pertinent global intelligence that can be used to improve current security infrastructure and controls.
-The “Sample Locker” for malware or File Lake
the safe repository for malware files that aids in training and future research. A thorough manifest is kept in the malware lab for searching through the locally and internationally sourced archived samples.
Repository for metadata or data lake
All of the metadata that is extracted during analysis is stored in this repository, where it can be found and hunted for at any time. The ability to detect changes in disposition over time and to hunt for latent threats retrospectively are both supported by applying YARA rulesets to historical data.
Rule Repository for YARA
Rulesets are gathered in a YARA repository for sharing and use in enhancing threat hunting and detection.
Since not all threat-hunting campaigns will be equally effective, it’s equally crucial to develop a plan for customizing threat-hunting initiatives as your business gains more knowledge about current data trends and adversaries. Tell your teams the truth about what’s working, what isn’t, and innovative ways to use machine learning and other tools to help you achieve your objectives.
Threat hunting is an effective addition to your security efforts when used in conjunction with offensive strategies. It should be considered a successful, all-encompassing security program’s keystone element and an ever-evolving strategic approach to identifying potential problems.