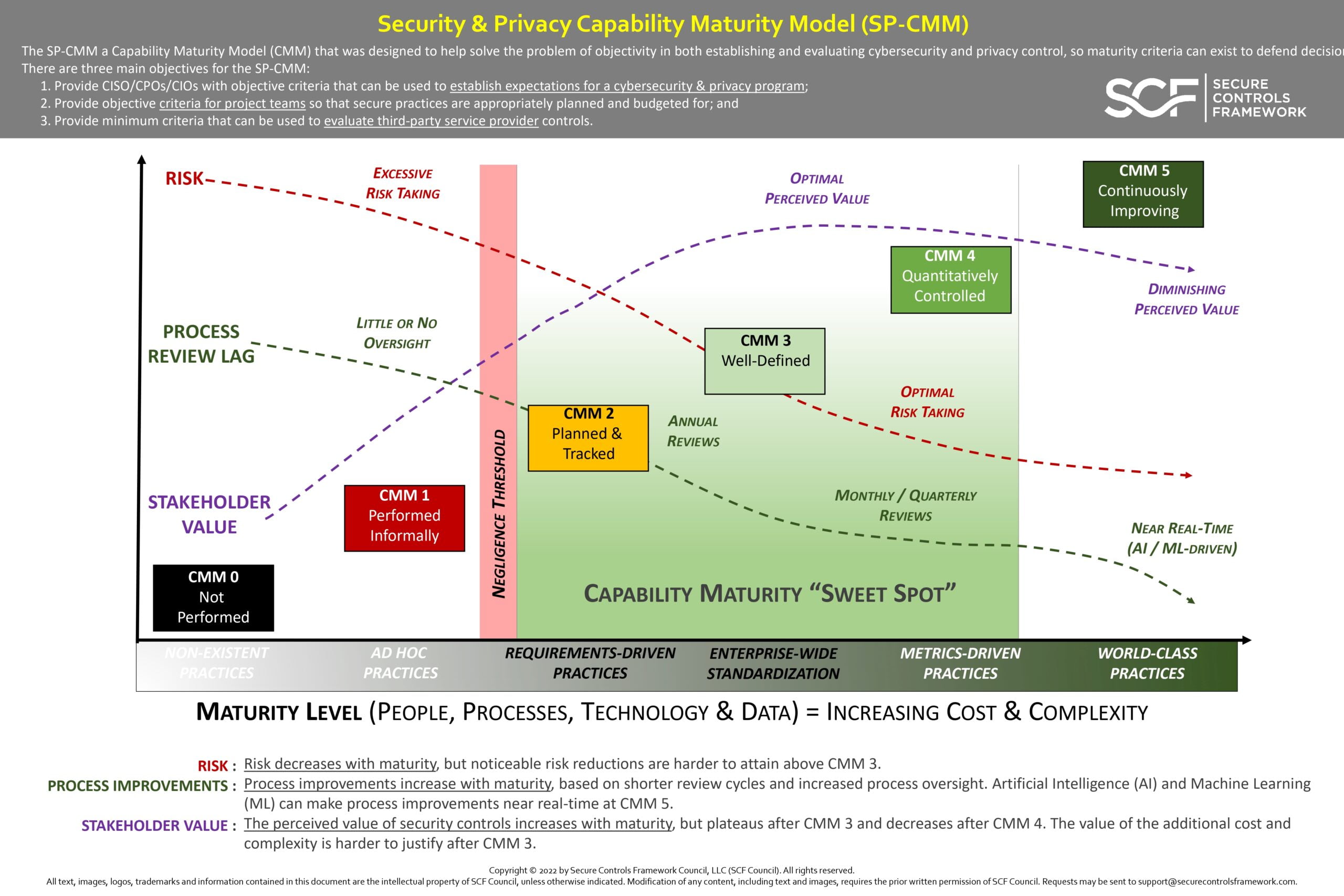
The S|P establishes 32 common-sense principles to guide the development and oversight of a modern security and privacy program. The S|P is sourced from the Secure Controls Framework (SCF), which is a free resource for businesses. The SCF’s comprehensive listing of over 1,000 cybersecurity andprivacy controls is categorized into 32 domains that are mapped to… Continue reading Security and Privacy Capability Maturity Model (SP-CMM) by SCF, Secure and Privacy by Design Principles Framework
Tag: ciso
A Successful Threat-Hunting Program’s Foundation
“Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses.” ~ Crowdstrike An increase in high-profile industry security issues over the past few years (PDF) has made… Continue reading A Successful Threat-Hunting Program’s Foundation