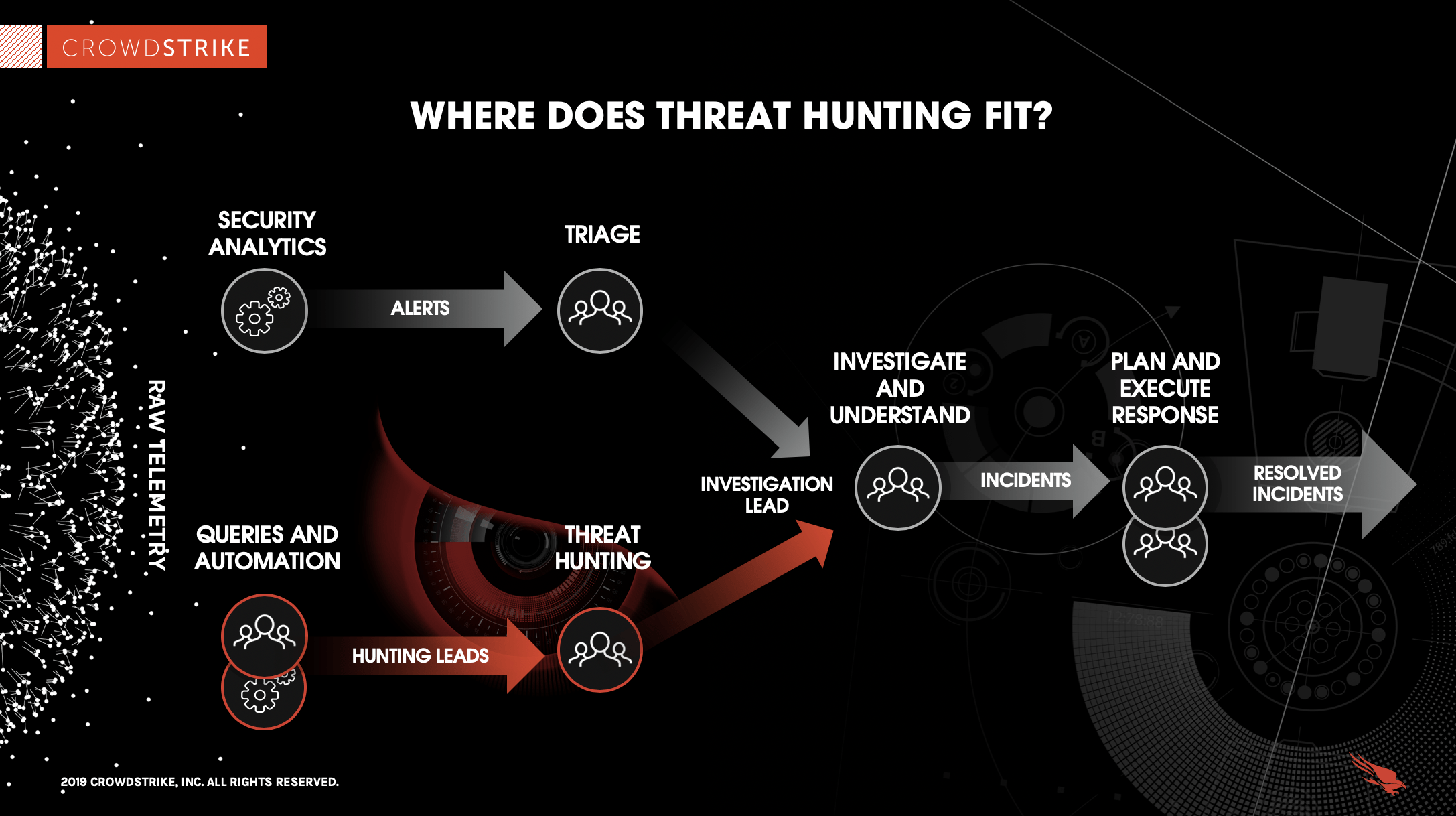
“Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses.” ~ Crowdstrike An increase in high-profile industry security issues over the past few years (PDF) has made… Continue reading A Successful Threat-Hunting Program’s Foundation
Month: September 2022
Feds and npm Give advice on supply chain security to prevent another SolarWinds incident
Faster development times, innovation, and a thriving open-source community have all been made possible by the ability to use another developer’s project as a dependency. With many JavaScript projects relying on tens or even hundreds of dependencies, the package ecosystem known as npm—which supports TypeScript and JavaScript projects—has expanded to include 2.1 million packages. The… Continue reading Feds and npm Give advice on supply chain security to prevent another SolarWinds incident
Change your Tiktok password immediately in case of a massive data leak.
There’s a post from 12 hours ago on a well-known hacking forum making some pretty significant claims, with the disclaimer that everything is “alleged” at this point:“We don’t know why it’s there or what it’s for, but we’re releasing a 34GB additional database called “cabinet cloud” from the Oracle server we’re using because we don’t… Continue reading Change your Tiktok password immediately in case of a massive data leak.
NATO Examines Data Breach from Missile Vendor on the Dark Web
One set of documents purportedly belonging to an EU defense supplier includes information on the weapons Ukraine used to fight Russia. According to a report in the media, NATO is looking into the leak of data that hackers are said to have purchased on the Dark Web from a European missile systems company. The stolen… Continue reading NATO Examines Data Breach from Missile Vendor on the Dark Web