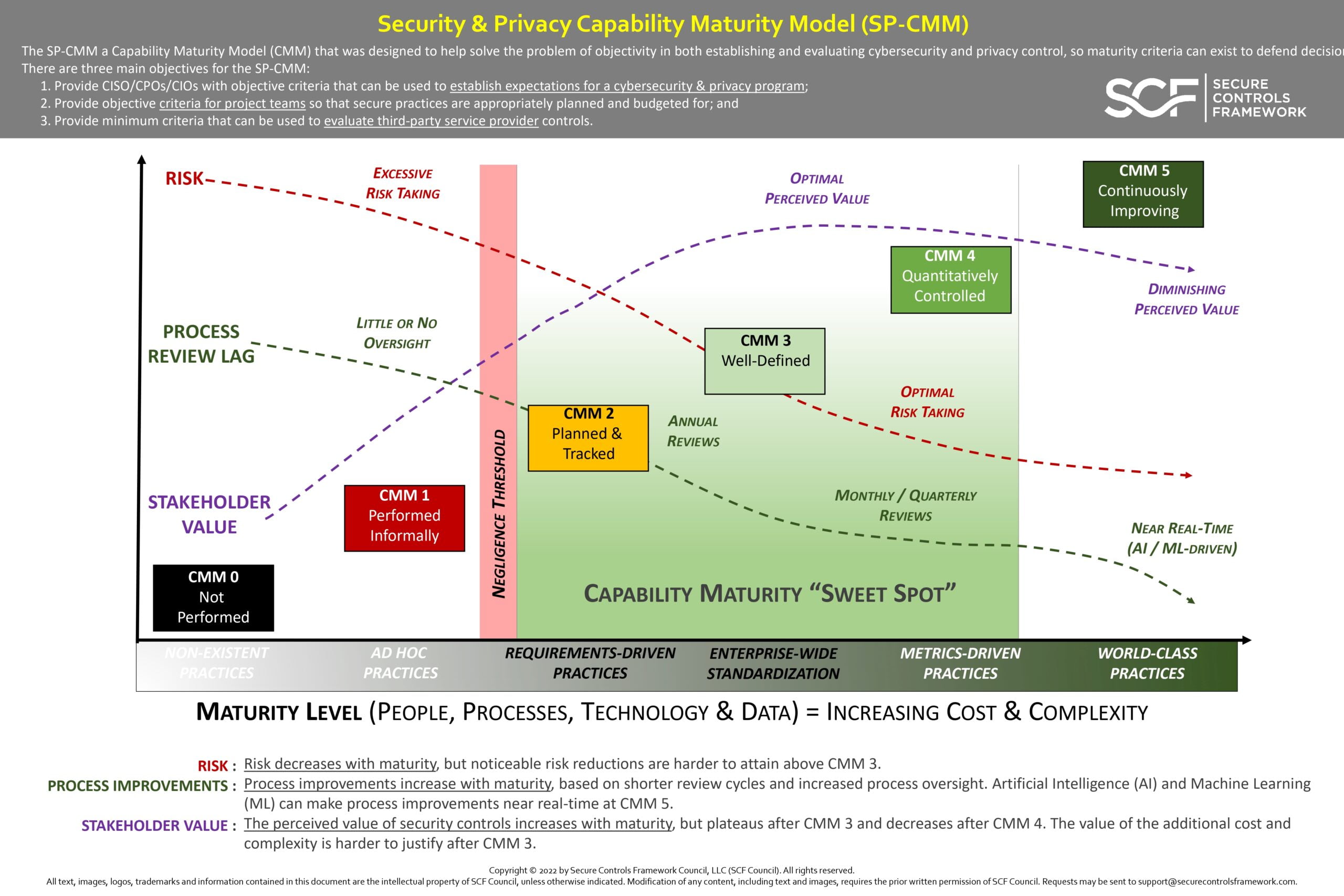
The S|P establishes 32 common-sense principles to guide the development and oversight of a modern security and privacy program. The S|P is sourced from the Secure Controls Framework (SCF), which is a free resource for businesses. The SCF’s comprehensive listing of over 1,000 cybersecurity andprivacy controls is categorized into 32 domains that are mapped to… Continue reading Security and Privacy Capability Maturity Model (SP-CMM) by SCF, Secure and Privacy by Design Principles Framework
Category: Defensive
Campaigns to be Introduced to MITRE ATT&CK V12
Primary Articles Published by Matt Malona In ATT&CK 2022 roadmap, at ATT&CKCon 3.0, and most recently on the SANS Threat Analysis Rundown, we’ve discussed incorporating campaigns into ATT&CK, but their release is soon approaching! Beginning with the release of ATT&CK v12 on October 25, you will be able to use the Campaigns structure for all… Continue reading Campaigns to be Introduced to MITRE ATT&CK V12
DevSecOps is not just a technological shift; it is also a cultural one, according to Tenable.cs Cloud Security’s whitepaper, “7 Habits of Highly Effective DEVSECOPS Teams.”
DecSecOps, which is typically viewed as an integrated team of development, operational, and security practitioners that can securely deliver innovation within a defined scope to market, is an ideal that organisations have been vying to achieve. Even though today’s complex, dynamic cloud native projects require this level of cooperation, the majority of contemporary organisations are… Continue reading DevSecOps is not just a technological shift; it is also a cultural one, according to Tenable.cs Cloud Security’s whitepaper, “7 Habits of Highly Effective DEVSECOPS Teams.”
BARK: A PowerShell script was created to aid the BloodHound Enterprise team in locating and regularly validating abuse primitives.
BloodHound Attack Research Kit is referred to as BARK. It is a PowerShell script created to help the BloodHound Enterprise team find and keep track of abuse primitives. At the moment, BARK is concentrated on Microsoft’s Azure family of goods and services. There are no external dependencies needed for BARK. The functions of BARK are… Continue reading BARK: A PowerShell script was created to aid the BloodHound Enterprise team in locating and regularly validating abuse primitives.
The Azure Threat Research Matrix is explained
It’s typical for the assessment team to cite the MITRE ATT&CK knowledge base when conducting an offensive security assessment so that high-level stakeholders can see visually which techniques were effective and administrators and defenders can comprehend the techniques used in order to correct or defend against them in the future. But there is no official… Continue reading The Azure Threat Research Matrix is explained
A Successful Threat-Hunting Program’s Foundation
“Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses.” ~ Crowdstrike An increase in high-profile industry security issues over the past few years (PDF) has made… Continue reading A Successful Threat-Hunting Program’s Foundation
Feds and npm Give advice on supply chain security to prevent another SolarWinds incident
Faster development times, innovation, and a thriving open-source community have all been made possible by the ability to use another developer’s project as a dependency. With many JavaScript projects relying on tens or even hundreds of dependencies, the package ecosystem known as npm—which supports TypeScript and JavaScript projects—has expanded to include 2.1 million packages. The… Continue reading Feds and npm Give advice on supply chain security to prevent another SolarWinds incident
Free Cybersecurity Services And Tools Released by CISA
CISA has collected a list of free cybersecurity tools and services to help companies advance their security capabilities as part of our ongoing objective to minimise cybersecurity risk among U.S. critical infrastructure partners and state, local, tribal, and territory governments. CISA’s cybersecurity services, widely used open source tools, and free tools and services given by… Continue reading Free Cybersecurity Services And Tools Released by CISA
Gartner EDRs are not perfect, fail against common attacks
Advanced Persistent threats have been a pain for blue teams for a very long time, and one of the key tool in the arsenal is Endpoint Detection and Response tools since the recent past, however, they come with their limitations as well. endpoint detection & response (EDR) software from 18 of today’s top cybersecurity firms… Continue reading Gartner EDRs are not perfect, fail against common attacks
NSA Released D3FEND a framework for cybersecurity professionals to tailor defenses
Recently a Framework was Released by NSA named D3FEND which is based on and Complementary to MITRE ATT&CK Framework. It gave a Technical Knowledge base to create Defensive Countermeasure against Common Offensive techniques. D3FEND, a framework for cybersecurity professionals to tailor defenses against specific cyber threats is now available through MITRE. NSA funded MITRE’s research… Continue reading NSA Released D3FEND a framework for cybersecurity professionals to tailor defenses